发行日期:2024年4月20日 版本号:2 修订号:4
lssue Date:April 20, 2024 Issue Number: 2 Revise No: 4
1. 目的 Purpose
为确保BOHAN提供信息安全管理体系(英文缩写ISMS,下同)认证过程的有效性,本文件规定了开展信息安全管理体系认证的基本过程和特定要求。
In order to ensure the effectiveness of information security management system (ISMS) certification process provided by BOHAN, this document specifies the basic process and specific requirements for information security management system certification.
2. 适用范围Scope of application
本文件适用于信息安全管理体系认证过程管理,仅包括ISO/IEC 27006:2015及 CNAS-SC170:2017、IAF_MD26的特殊要求,对于ISO17021的通用要求已在G-BOHAN-UD-01~20程序中说明,此处不再详述。
This document is applicable to the management of information security management system certification process, only including the special requirements of ISO / IEC 27006:2015 and CNAS-SC170:2017,IAF_MD26. The general requirements of ISO17021 have been described in G-BOHAN-UD-01 ~ 20 procedure, and will not be detailed here.
3职责responsibilities
3. 1市场部门负责客户接洽、市场开发与合同接收、签订,负责认证证书发送和回收过程中的联络。
The marketing department is responsible for customer contact, market development, contract receiving and signing, and the contact in the process of certification certificate sending and recycling.
3. 2技委会负责组织合同评审;负责审核资料的跟踪、验收与归档管理和组织审核资料认证决定的评定;以及向CNAS/IAS报送与认证有关的信息;负责对认证实施过程的监控。负责对审核和认证人员的能力评定。
The technical committee is responsible for organizing the contract review; Responsible for the tracking, acceptance and filing management of audit data, and organizing the evaluation of audit data certification decision; And submit certification related information to CNAS and IAS; Responsible for monitoring the implementation process of certification. Responsible for the ability evaluation of audit and certification personnel.
3. 3审核部负责编制审核方案,进行审核准备,组成审核组实施现场审核,和对审核过 程的监督与控制;负责对审核人员的管理。
The audit department is responsible for preparing the audit plan, preparing for the audit, forming an audit team to carry out on-site audit, and supervising and controlling the audit process; Responsible for the management of audit personnel.
3. 4客服部、技委会负责获证客户的注册管理。
The customer service department and the technical committee are responsible for the registration management of certified customers.
3. 5合同评审人员和审核方案管理人员在进行人员评定时统称为项目管理人员。
Contract review personnel and audit scheme management personnel are collectively referred to as project management personnel in personnel evaluation.
3. 6管理部负责认证证书的制作;
The Management Department is responsible for the production of certification certificate;
3. 7总经理负责认证证书的签发和认证注册资格(包括授予、保持、更新、扩大、缩小、 暂停和撤销认证)的批准。
The general manager is responsible for the issuance of certification certificates and the approval of certification registration qualifications (including granting, maintaining, updating, expanding, narrowing, suspending and revoking certification).
4程序和要求Procedures and requirements
4. 1认证人员能力评价Competency evaluation of certification personnel
4. 1. 1 基本要求:按照以下原则分别对各类人员的能力进行初始评价、初始测试、能力监控与评价,能力定期测试与评价,并保持评价记录。认证审核员、认证管理人员能力评价结果需经由领导批准后方可在系统上录入。
Basic requirements: carry out initial evaluation, initial test, ability monitoring and evaluation of all kinds of personnel according to the following principles, and regularly test and evaluate the ability, and keep evaluation records. The ability evaluation results of certification auditors and certification management personnel can be input into the system only after being approved by leaders.
4. 1. 2认证通用知识和技能见附录B。See Appendix B for general knowledge and skills of certification.
4. 1. 3认证人员能力初始评价Initial evaluation of certification personnel's ability
4. 1. 3. 1认证人员初始能力评价
Initial ability evaluation of certification personnel
a. 所有认证人员的知识和能力要求、特定技能要求等,须满足准ISO/IEC 17021-1:2015《合格评定管理体系审核与认证机构的要求 第1部分:要求》(CNAS-CC01:2015)及CNAS-CC170:2015《信息安全管理体系认证机构要求》(ISO/IEC 27006:2015)对认证人员的相关知识和能力要求。
The knowledge and ability requirements, specific skill requirements, etc. of all certified personnel must meet the requirements of the quasi-ISO/IEC 17021-1:2015 "Requirements for Conformity Assessment Management System Audit and Certification Bodies Part 1: Requirements" (CNAS-CC01:2015) and CNAS-CC170:2015 "Requirements for Information Security Management System Certification Bodies" (ISO/IEC 27006:2015) requires relevant knowledge and competency of certification personnel.
b. 由管理部根据初始能力评价准则进行初始能力评价前的人事确认并记录,记录包括被评价人的教育、工作、培训、审核(咨询)的相关信息,填写《认证人员登记表》、《审核员/技术专家审核经历汇总表》(审核员专用)以获取其知识和技能的证据,使对其能力有基本了解;《认证人员登记表》内容尽可能详细、充分、以便于识别被评价人员所具有的知识和技能;
The Management Department shall confirm and record the personnel before the initial ability evaluation according to the initial ability evaluation criteria. The records include the education, work, training and audit (consultation) information of the evaluated person, and fill in the registration form of certification personnel and the audit experience summary form of auditors / technical experts (for auditors only) to obtain the evidence of their knowledge and skills, To have a basic understanding of it; The contents of the certification personnel registration form should be as detailed and sufficient as possible to identify the knowledge and skills of the evaluated personnel;
c. 管理部应在招聘人员入职时进行基本的面试考察,以了解其过去的工作经历知识
和技能的情况;将面试情况记录在《管理体系认证人员面试报告》中,必要时对记录中相关信息进行验证、澄清和确认;
The Management Department should conduct basic interviews and inspections when recruiting personnel to understand their past work experience, knowledge, and skills; Record the interview situation in the "Interview Report for Management System Certification Personnel", and verify, clarify, and confirm the relevant information in the record if necessary;
d. 技术委员会获得管理部的上述有关材料记录后,组织评价人员根据本程序规定的评价准则、《信息安全管理体系专业技术领域分析》对审核员进行初始能力评价,将评价结果填写在《认证人员专业能力评价表》中。
After the technical committee obtains the above-mentioned relevant material records of the Management Department, it shall organize the evaluators to carry out the initial ability evaluation for the auditors according to the evaluation criteria specified in this procedure and the analysis of the professional technical field of information security management system, and fill the evaluation results in the professional competence evaluation form of certified personnel.
e. 技委会对批准评价合格的认证人员分别建档编制最新评价结果和注册状态,之后准备进入认证人员初始能力测试程序。
The technical committee shall file and compile the latest evaluation results and registration status of the qualified certification personnel, and then prepare to enter the certification personnel initial ability test procedure.
4. 1. 3. 2认证人员初始能力测试
Initial competency test of certified personnel
4. 1. 3. 2. 1审核员/技术专家的初始能力测试
Initial competency test of Auditor / technical expert
a. 技委会根据《认证人员专业能力评价表》所输出的认证业务范围(对应的技术领域),依据《信息安全管理体系专业技术领域分析》中有关的知识内容编制并提供一份《审核员认证管理人员专业能力测试表》做测试,并交回技委会。经技委会评价,管理者代表审批,审定符合要求报总经理批准即认定该审核员能力合格可安排其参加审核。如测试结果为不合格的,则需要对该工作岗位进行特定知识和技能的专项培训并再考核合格后方可参加审核。
According to the certification business scope (corresponding technical field) output by the "professional competence evaluation form of certification personnel" of "d", a "professional competence test form for auditor certification management personnel" is prepared and provided according to the relevant knowledge content in "analysis of professional technical field of information security management system" for testing, and submit it to the technical committee. According to the evaluation of the technical committee, The management representative shall examine and approve, and report to the general manager for approval, that is to say, the ability of the auditor is qualified, and the auditor can be arranged to participate in the audit. If the test result is unqualified, special training on specific knowledge and skills is required for the post, and the review can only be conducted after passing the re examination.
b. 级别审核员首次参加博瀚审核,需由具有组长资格的人员进行见证,并填写《机构内部新入职审核员初始能力见证评价报告》。见证不合格者需重新安排见证或经专项培训考核合格后方可正式执行审核任务。CCAA见证可替代首次见证。特殊情况由体系事业部负责人批准。
The auditor participated in Bohan audit for the first time shall be witnessed by the lead auditor qualification and fill in the CCAA registration management system certification witness review report. If the witness fails to pass the examination, it is required to arrange the witness again or pass the special training examination before the formal audit task can be carried out. CCAA witness can replace the first witness. Special circumstances shall be approved by the person in charge of the system division.
4. 1. 3. 2. 2项目管理员(申请/合同评审人员、计划/方案管理人员)的初始能力测试
Initial competency testing of project managers (application / contract reviewers, program / program managers)
a. 纳入《认证人员一览表》备案的项目管理人员,由技委会依据《信息安全管理体系专业技术领域分析》中有关的知识内容编制并提供一份《审核员认证管理人员专业能力测试表》做测试,并交回技委会。经技委会评价,管理者代表审批,审定符合要求报总经理批准即认定该项目管理员具备相应专业能力。如评价、测试结果为不合格的,则需要对该工作岗位进行特定知识和技能的专项培训并再考核合格后方可上岗。
For the project management personnel included in the list of certification personnel, the technical committee shall prepare and provide a test form for professional competence of auditor certification management personnel according to the relevant knowledge content in the analysis of professional and technical fields of information security management system for testing, and submit it to the technical committee. Evaluated by the technical committee, approved by the management representative, If it meets the requirements and is submitted to the general manager for approval, the project manager will be recognized as having the corresponding professional ability. If the post is not qualified, it can be evaluated for the specific knowledge and skills.
4. 1. 3. 2. 3报告检查/认证决定人员的初始能力测试
Report initial competency test of inspection / certification decision maker
a. 纳入《认证人员一览表》备案的报告检查/认证决定人员,技委会根据的《认证人员专业能力评价表》所输出的认证业务范围(对应的技术领域),依据《信息安全管理体系专业技术领域分析》中有关的知识内容编制并提供一份《审核员认证管理人员专业能力测试表》做测试,并交回技委会。经技委会评价,管理者代表审批,审定符合要求报总经理批准即认定该报告检查/认证决定人员具备相应专业能力。如评价、测试结果为不合格的,则需要对该工作岗位进行特定知识和技能的专项培训并再考核合格后方可上岗。
The technical committee shall, according to the certification business scope (corresponding technical field) output by the certification personnel professional ability evaluation form of D, According to the relevant knowledge content in the analysis of professional and technical fields of information security management system, a professional competence test form for auditor certification management personnel is prepared and provided for testing, and submitted to the technical committee. Evaluated by the technical committee, approved by the management representative, If the report meets the requirements and is submitted to the general manager for approval, it will be recognized that the person making the inspection / certification decision of the report has the corresponding professional competence. If the evaluation and test results are unqualified, special training on specific knowledge and skills is required for the post, and the post can only be employed after passing the re examination.
4. 1. 3. 2. 4能力评价人员的初始能力测试Initial competency test of competency evaluators
a. 纳入《认证人员一览表》备案的能力评价人员,由管理者代表依据《信息安全管理体系专业技术领域分析》中有关的知识内容编制并提供一份《审核员认证管理人员专业能力测试表》做测试,并交回技委会。经技委会评价,管理者代表审批,审定符合要求报总经理批准即认定该能力评价人员具备相应专业能力。如评价、测试结果为不合格的,则需要对该工作岗位进行特定知识和技能的专项培训并再考核合格后方可上岗。
For the competence evaluation personnel included in the list of certification personnel, the management representative shall prepare and provide a test form for professional competence of auditor certification management personnel according to the relevant knowledge content in the analysis of professional and technical fields of information security management system for testing, and submit it to the technical committee. Evaluated by the technical committee, approved by the management representative, If the assessment meets the requirements and is submitted to the general manager for approval, it is recognized that the assessment personnel have the corresponding professional ability. If the evaluation and test results are unqualified, special training on specific knowledge and skills is required for the post, and the post can only be employed after passing the re examination.
4. 1. 4认证人员工作过程中的能力监控与评价
Ability monitoring and evaluation of certification personnel in the working process
4. 1. 4. 1工作过程中能力监控评价是通过在认证人员日常实际工作、审核中的能力表现 予以多方式的证实其能力是否得到保持。
The ability monitoring and evaluation in the process of work is to confirm whether the ability is maintained through the ability performance of the certification personnel in the daily actual work and audit.
4. 1. 4. 2对审核项目中审核员(含实习审核员)、技术专家的审核工作的专业能力和合规性的过程监控评价。于每一个审核项目中,由审核组长现场按照规定的考察项目实施并记录在《机构内部审核员见证评审报告》中。如现场表现见证评价结果出现一项为“较差”或“差”的,则需要对该审核人员进行补充培训及考核。
Process monitoring and evaluation on professional ability and compliance of auditors (including intern auditors) and technical experts in audit projects. In each audit project, the audit team leader shall implement the inspection items according to the regulations and record them in the internal auditor witness review report of the organization. If there is one item of "poor" or "poor" in the field performance witness evaluation results, supplementary training and assessment shall be conducted for the audit personnel.
4. 1. 4. 3委托客户对审核组成员的工作表现及能力的过程监控评价。所有的认证审核项目结束后,在客户获证后由客服人员与认证组织联系,提供一份《认证组织满意度调查表》(评价对象为公司的项目管理人员及本次审核的审核组各成员),请获证组织在对公司信息沟通、审核组成员在审核工作的专业性、工作能力和合规性、服务质量等进行评定。客服部收回调查评价表后进行统计分析,对评价不合格的当事人,应视为客户投诉处理,按照相关程序要求进行处理。
Entrust client to monitor and evaluate the work performance and ability of audit team members. After the completion of all certification audit projects, the customer service personnel shall contact the certification organization and provide a "certification organization satisfaction questionnaire" (the evaluation object is the project management personnel of the company and each member of the audit team), The certified organization is requested to evaluate the company's information communication, the professionalism, working ability and compliance of audit team members, and service quality. After the customer service department takes back the survey and evaluation form, the client who fails to pass the evaluation shall be treated as a customer complaint and handled according to the relevant procedure requirements.
4. 1. 5认证人员的能力定期测试及评价
Periodic evaluation of qualification personnel
4.1. 5. 1审核员的年度见证考核Auditor annual witness
公司根据审核人员使用频率和活动的风险水平,策划审核人员的见证频率,具体见《审
核人员管理办法》。
According to the auditors use frequency and activity risk level, BOHAN evaluate the auditor witness plan, see for " Measures for Administration of Audit Personnel ".
4. 1. 5. 2对关键岗位人员(项目管理人员、认证决定人员、能力评价人员)的能力进行年度确认每年1-2月技委会、审核部组成评价组,按照《认证管理人员专业能力评价表》对关键岗位人员进行考评。对测试不合格的关键岗位人员,技委会将撤销其相应的技术领域中的业务代码范围。
The ability of key post personnel (project management personnel, certification decision-making personnel, ability evaluation personnel) shall be confirmed annually. From January to February each year, the technical committee and the audit department shall form an evaluation group to evaluate the personnel in key positions according to the professional ability evaluation form for certification management personnel. For the key personnel who fail to pass the test, The technical committee will withdraw the business code scope in its corresponding technical field.
4. 1. 6审核员初次担任组长的能力评价
Evaluation of auditor's ability to serve as team leader for the first time
4. 1. 6. 1级别审核员初次担任组长的,需要对其组长资格的能力进行一次见证评价。申请人需填写《审核员见证申请表》,经在审核任务批准后由审核部安排见习组长作为审核组的组长开展审核。现场见证人员为具有注册审核员资格及组长资格的审核人员。现场见证后见证员填写《机构内部审核组长见证评价报告》;
The qualification of the auditor to be the first auditor. The applicant should fill in the application form for auditor witness. After the audit task is approved, the audit department will arrange the trainee team leader as the leader of the audit team to carry out the audit. The on-site witness is the auditor with the qualification of Registered Auditor and team leader. After the scene witness, the witness shall fill in the internal audit team leader of the organization witnessed the evaluation report;
4. 1. 6. 2级别审核员的组长资格的能力见证原则为一次见证,对见证结论最终意见为不合格的,需提出申请再次见证直至见证结论最终意见为合格,审核部才能在后续安排审核项目时给与其组长角色。
The ability witness principle of the team leader qualification of the level auditor is one-time witness. If the final opinion of the witness conclusion is unqualified, an application for re witness is required. Until the final opinion of the witness conclusion is qualified, the audit department can play a role with the team leader in the subsequent audit project arrangement.
4. 1. 7能力评价负面结果的处理
Handling of negative results of competency assessment
4. 1. 7. 1公司在认证业务范围认可后,对某一唯一性特定技术领域认证人员能力评价的结果为不满意的,且通过后续的培训依然不能满足要求的,或是如具备某一特定技术领域的专业能力审核员,被公司解雇的,将对公司的能力产生影响。技术委员会应及时报告管理者代表或总经理,并分析对公司整体能力的限制性因素和对目前认证产生的影响;
After the certification business scope is approved, the company is not satisfied with the result of the ability evaluation of a unique and specific technical field certification personnel, and still can not meet the requirements through the follow-up training, or if the company has a professional competence auditor in a specific technical field and is dismissed by the company, the company's ability will be affected. The technical committee shall report to the management representative or general manager in a timely manner, and analyze the restrictive factors on the overall ability of the company and the impact on the current certification;
4. 1. 7. 2通过分析,批准后由管理部快速招聘具备特定技术领域认证人员予以补充,技 术委员会并按照本程序有关要求进行对其初始能力评价。
After analysis and approval, the Management Department shall quickly recruit the personnel with certification in specific technical field to supplement, and the technical committee shall evaluate the initial ability according to the relevant requirements of this procedure.
4. 1. 8认证人员能力评价准则的确定
Determination of competency evaluation criteria for certification personnel
4. 1. 8. 1申请/合同评审人员的能力准则:
Competency criteria for application / contract reviewers:
a. 具有大学专科以上学历,有两年以上工作经历;b. 熟悉、理解“认证认可条例”、“认可机构认可准则、规则、指南”的要求及公司的相关认证审核程序、申请和合同评审作业认证制度的规定; c. 掌握负责评审的体系标准或其他规范性文件内容,了解相关法律法规的要求:认证过程中所用的相关ISMS标准和其他规范性文件; d. 熟悉国民经济专业分类和机构各体系技术领域分类分组和管理要求的内容; e. 能熟练使用机构计算机管理系统。 f. 熟悉相关行业实践的通用术语和过程、技术和风险的理解(不具备时可由相应专业专家协同);g. 熟悉客户产品、过程和组织类型、规模、治理、结构方面内容(不具备时可由相应专业专家协同)。h. 如申请/合同评审人员同时为审核员时,对其审核员资格的评价可替代认证管理人员的能力评价。
College degree or above, more than two years working experience; b. Be familiar with and understand the requirements of "Regulations on certification and Accreditation", "accreditation criteria, rules and guidelines for accreditation institutions" and the relevant certification procedures, application and contract review operation certification system of the company; c. Master the contents of system standards or other normative documents in charge of review, Understand the requirements of relevant laws and regulations:Relevant ISMS standards and other normative documents used in the certification process; d. Be familiar with the classification of national economy and the contents of technical field classification and management requirements of various systems of institutions; e. Be familiar with computer management system. f. Familiar with general terms and process understanding,technology, risk of relevant industry practice (if not available, it can be coordinated by relevant professional experts); g. Familiar with customer product, process and organization type, scale, governance and structure (if not available, it can be coordinated by corresponding professional experts). h. If the application / contract reviewer is also an auditor, the evaluation of the auditor qualification can replace the ability evaluation of the certification manager.
4. 1. 8. 2审核方案管理人员(包括确定审核项目、指派审核任务人员)的能力准则:
Competency criteria for audit scheme management personnel (including determining audit items and assigning audit task personnel)
a. 具有大学专科以上学历,有两年以上工作经历;b. 具有一定的分析、判断能力及良好的口头和文字表达能力;c. 有良好的服务意识,有责任心、有耐心,能与客户进行良好的沟通。 d. 熟悉理解“认证认可条例”、“认可机构认可准则、规则、指南”的要求及公司认证审核程序及有关认证管理制度的相关规定;e. 了解各标准体系基本内容; f. 能熟练运用机构计算机管理系统。 g. 17021要求的其他知识和技能。
At least two years of college education and working experience; b. Have a certain ability of analysis, judgment and good oral and written expression ability; c. Good sense of service, sense of responsibility, patience, good communication with customers. d. Be familiar with the requirements of "Regulations on certification and Accreditation", "accreditation criteria, rules and guidelines for accreditation bodies", as well as the company's certification audit procedures and relevant provisions of certification management system; e. Understand the basic content of each standard system; f. Be proficient in using computer management system. g. Other knowledge and skills required by 17021.
h. 如审核方案管理人员同时为审核员时,对其审核员资格的评价可替代其认证管理人员的能力评价。
If the audit scheme manager is also an auditor, the evaluation of the auditor qualification can replace the ability evaluation of the certification manager.
4. 1. 8. 3报告检查/认证决定人员评定准则:
Evaluation criteria for report inspection / certification decision personnel:
a. 具有大学专科以上学历,有两年以上工作经历;b. 掌握信息安全管理体系标准或其他规范性文件内容,了解相关法律法规的要求;熟悉审核原则、实践和技巧;熟悉有相关行业实践的通用术语和过程内容;熟悉信息安全管理相关的术语和定义(包括:范围和删减的适用性);信息安全管理的相关工具、方法、技术及其在认证过程中的应用的影响;c. 其他知识和技能(包括信息安全管理术语、原则、实践和技术:ISMS 特定文件的结构、层级和相互关系;信息安全风险评估和风险管理;ISMS 适用的过程等);d. 具备与相关业务领域实践有关的通用术语和风险及客户的产品、过程、组织类型、规模、治理、结构、职能和关系的知识;e. 特殊行业/高风险行业认证业务范围的认证决定人员宜具备不低于该业务范围专业审核员的要求;一般行业/中低风险行业认证业务范围的认证决定人员宜具备专业大类中的某一专业小类相关审核员的能力要求;f. 认证评定亦可由级别审核员与该专业的技术专家一同做出认证决定,具体专业评定要求见附录D;g. 如报告检查/认证决定人员同时为审核员时,对其审核员资格的评价可替代其认证管理人员的能力评价。
Having a college degree or above and at least two years of work experience; b. Master the content of information security management system standards or other normative documents, and understand the requirements of relevant laws and regulations; Familiar with audit principles, practices, and techniques; Familiar with general terminology and process content with relevant industry practices; Familiar with terms and definitions related to information security management (including scope and applicability of deletions); The impact of tools, methods, technologies related to information security management and their application in the authentication process; c. Other knowledge and skills (including information security management terminology, principles, practices, and techniques: structure, hierarchy, and interrelationships of ISMS specific documents; information security risk assessment and risk management; processes applicable to ISMS, etc.); d. Having knowledge of common terminology and risks related to relevant business practices, as well as customer products, processes, organizational types, scales, governance, structures, functions, and relationships; e. The certification decision personnel for the special/high-risk industry certification business scope should have the requirements of no less than professional auditors for that business scope; The certification decision personnel in the general industry/medium and low risk industry certification business scope should have the ability requirements of auditors related to a certain professional subcategory in the professional category; f. Certification evaluation can also be made by level auditors and technical experts in the field together, and specific professional evaluation requirements can be found in Appendix D; g. When the report inspection/certification decision personnel are both auditors, the evaluation of their auditor qualifications can replace the ability evaluation of their certification management personnel.9
4. 1. 8. 4负责实施专业能力评价的人员评价准则:
Evaluation criteria for personnel responsible for implementing professional competence evaluation:
a.具有相应专业技术领域的基本理论知识;
Have basic theoretical knowledge of corresponding professional and technical fields;
b.熟悉机构专业能力评价准则、证实方法;
Be familiar with the evaluation criteria and verification methods of professional competence;
c.具有一定的分析、判断能力;
Have a certain ability of analysis and judgment;
d.熟悉国民经济专业分类和机构各体系技术领域分类分组和管理要求的内容;
Be familiar with the classification of national economy and the contents of technical field classification and management requirements of various systems of institutions;
e.如专业能力评价人员同时为审核员时,对其审核员资格的评价可替代其认证管理 人员的能力评价。
If the professional competence evaluator is an auditor at the same time, the evaluation of the auditor qualification can replace the ability evaluation of the certification manager.
4. 1. 8. 5审核人员、技术专家能力评价准则:
Competence evaluation criteria for auditors and technical experts:
a. 教育:与信息安全技术相关的专业的本科学历;
Education: Bachelor degree in information security technology related major;
b. 工作经历:至少4年信息技术方面全职实际工作经历,其中至少2年的工作经历来自与信息安全有关的职责或职能;
Work experience: at least 4 years of full-time practical work experience in information technology, of which at least 2 years work experience comes from information security related responsibilities or functions;
c. 审核员培训:成功完成5天或40小时的ISMS审核员培训;
Auditor Training: successfully completed 5 days or 40 hours of ISMS auditor training;
d. 审核经历:参加审核总天数至少10天,其中包括文件评审、风险分析的评审、现场审核和审核报告。
Audit experience: the total audit days shall not be less than 10 days, including document review, risk analysis review, on-site audit and audit report.
e. 能够广泛、透彻地认识复杂的运作,并理解在较大的客户组织中各单元的职能;
Have a broad and thorough understanding of complex operations and understand the functions of units in larger customer organizations;
f. 通过持续的专业发展,保持最新的信息安全和审核的知识与技能。
Maintain up-to-date information security and audit knowledge and skills through continuous professional development.
g. 能力要求Capability requirements:
1、总体要求:具备信息安全的知识、与受审核的活动相关的技术知识、管理体系的
知识、审核原则的知识、ISMS监视/测量/分析和评价的知识等;
Overall requirements: possessing knowledge of information security, technical knowledge
related to the audited activities, knowledge of management systems, knowledge of audit principles, knowledge of ISMS monitoring/measurement/analysis and evaluation, etc;
2、信息安全管理术语、原则、实践和技术:审核组所有成员作为一个整体,应具备
:①ISMS特定文件的结构、层级和相互关系;②信息安全管理相关的工具、方法、技术及其应用;③信息安全风险评估和风险管理;④ISMS适用的过程;⑤当前可能与信息安全相关的或可能面临信息安全问题的技术。每个审核员应满足①、③和④。
Information security management terminology, principles, practices, and techniques: All members of the audit team as a whole should have: ① the structure, hierarchy, and interrelationships of ISMS specific documents; ② Tools, methods, technologies, and applications related to information security management; ③ Information security risk assessment and risk management; ④ The process applicable to ISMS; ⑤ Current technologies that may be related to information security or may face information security issues. Each auditor should meet the requirements of ①, ③, and ④.
3、理解网络结构与通信基础、数据安全、载体安全、环境安全、边界安全、应用安全
等相关技术。
Understand network architecture and communication infrastructure, data security, carrier security, environmental security, border security, application security, and other related technologies.
4、掌握与组织业务活动相关的知识,如流程、资产、风险、安全要求、控制措施以及信息安全技术和信息技术在业务活动中的特定应用等方面的知识。
Master knowledge related to the organization's business activities, such as processes, assets, risks, security requirements, control measures, and specific applications of information security technology and information technology in business activities.
5、掌握信息安全管理相关的法律法规及其他相关要求:参与ISMS审核的审核员应掌握ISO/IEC 27001的所有要求;审核组所有成员作为一个整体,应具有ISO/IEC 27002(如确定有必要,还可来源于行业特定标准)中的所有控制及其实施的知识。
Master laws, regulations, and other relevant requirements related to information security management:Auditors participating in ISMS audits should master all the requirements of ISO/IEC 27001; All members of the audit team as a whole should have knowledge of all controls and their implementation in ISO/IEC 27002 (or industry specific standards if necessary).
注:ISO/IEC 27002的控制类别有:信息安全策略、信息安全组织、人力资源安全、资产管理、访问控制,包括鉴别、密码、物理和环境安全、运行安全,包括IT服务、通讯安全,包括网络安全管理和信息传输、系统获取、开发和维护、供应商关系,包括外包服务、信息安全事件管理、业务连续性管理的信息安全方面,包括冗余、符合性,包括信息安全评审等。
Note: The control categories of ISO/IEC 27002 include: information security strategy, information security organization, human resource security, asset management, access control, including authentication, password, physical and environmental security, operational security, including IT services, communication security, including network security management and information transmission, system acquisition, development and maintenance, supplier relations, including outsourcing services, information security event management The information security aspects of business continuity management include redundancy, compliance, and information security reviews.
6、掌握信息安全管理体系相关标准、规范性文件、专业知识和相关法律法规在审核实践中的综合应用技能。
Master the comprehensive application skills of information security management system related standards, normative documents, professional knowledge, and relevant laws and regulations in audit practice.
7、掌握业务管理实践的知识:参与ISMS审核的审核员,应具有行业的信息安全最佳实践和信息安全规程、信息安全的策略和业务要求、通用业务管理的概念、实践,以及方针、目标和结果之间的关系、管理过程和相关的术语等相关的知识。
Mastering knowledge of business management practices: Auditors participating in ISMS
audits should have knowledge of industry best practices and information security regulations, information security policies and business requirements, general business management concepts and practices, as well as the relationship between policies, objectives, and results, management processes, and related terminology.
8、掌握客户的业务领域的知识:参与ISMS审核的审核员,应具有特定的信息安全领域、地域和管辖范围的法律法规要求、与业务领域相关的信息安全风险、与客户业务领域相关的通用术语、过程和技术、相关业务领域的实践的相关知识。
Mastering knowledge of the client's business domain: Auditors participating in ISMS audits
should have relevant knowledge of specific information security fields, geographical and jurisdictional legal and regulatory requirements, information security risks related to the business domain, general terminology, processes and technologies related to the client's business domain, and practices in related business domains.
9、掌握客户的产品、过程和组织相关的知识:审核组所有成员作为一个整体,应具有组织类型、规模、治理、结构、职能和关系,对开发和实施ISMS和认证活动的影响,包括外包;广义上的复杂运营;适用于产品或服务的法律法规要求等方面的知识。
Mastering knowledge related to customers' products, processes, and organizations: All
members of the audit team as a whole should have organizational type, scale, governance, structure, functions, and relationships, and their impact on the development and implementation of ISMS and certification activities, including outsourcing; Complex operations in a broad sense; Knowledge of legal and regulatory requirements applicable to products or services.
(技术专家的专业能力要求与审核员的专业能力要求一致。提供技术培训的,应有充分证据证明技术培训的有效性。)
(The professional competence requirements of technical experts are consistent with those of auditors. If technical training is provided, sufficient evidence shall be provided to prove the effectiveness of technical training. )
4.1.9 审核组长的能力评价准则Evaluation criteria for the ability of the audit team leader:
除4.1.8.5中的相关要求外,审核组长应满足以下要求In addition to the relevant requirements in 4.1.8.5, the audit team leader should meet the following requirements:
a)具备管理认证审核过程和审核组的知识和技能;Having knowledge and skills in managing certification audit processes and audit teams;
b)具备有效的口头和书面沟通能力。Have effective oral and written communication skills.
4. 2认证人员能力的保持与发展Maintenance and development of certification personnel's ability
4. 2. 1持续专业发展方式Sustainable professional development mode
审核员和其他认证人员可以通过博瀚提供持续专业发展机会以及自学等方式获得专业持续发展:
Auditors and other certification personnel can obtain professional sustainable development through BOHAN's continuous professional development opportunities and self-study
4. 2. 1. 1获取工作经验;
Obtain work experience;
4. 2. 1. 2辅导;
Coaching;
4. 2. 1. 3交流和研讨。
Communication and discussion.
4. 2. 2持续专业培训包括但不仅限于以下内容:
The continuing professional training includes but is not limited to:
4. 2. 2. 1技术领域能力准则的最新要求;
The latest requirements of competence criteria in the technical field;
4. 2. 2. 2博瀚关于ISMS审核和认证的最新要求;
The latest requirements of BOHAN on ISMS audit and certification;
4. 2. 2. 3通过能力评价发现,审核员或其他认证人员的实际能力不能完全满足能力准则 的要求,应对不满足的部分予以培训。
It is found that the actual ability of the auditor or other certification personnel can not fully meet the requirements of the competency criteria through the competency evaluation, and the unsatisfied part should be trained.
4. 2. 3在组织交流和研讨时,博瀚将考虑以下因素,以确保交流和研讨活动的有效性:
When organizing communication and discussion, BOHAN will consider the following factors to ensure the effectiveness of communication and discussion activities:
4. 2. 3. 1 博瀚审核和认证活动的范围、规模和绩效;
Scope, scale and performance of BOHAN audit and certification activities;
4. 2. 3. 2在必要时将交流和研讨的成果汇总,制定或修订相关文件,如: 技术领域能力分析报告、能力评价准则、审核和认证的程序、审核作业指导文件等。
When necessary, summarize the results of communication and discussion, formulate or revise relevant documents, such as capability analysis report in technical field, capability evaluation criteria, audit and certification procedures, audit operation guidance documents, etc.
4.2.4 ISO/ IEC 27001:2022 换版的能力要求Capability requirements for ISO/IEC 27001:2022 version change
4.2.4.1 各类认证职能人员(合同评审人员、审核方案管理人员、认证决定/报告复核人员、认证规则和方案制定人员、能力评价人员)应熟悉和理解ISO/IEC 27001:2022标准及ISO/IEC 27002:2022标准的变化。Various certification functional personnel (contract reviewers, audit scheme managers, certification decision/report reviewers, certification rules and scheme developers, and competency evaluators) should be familiar with and understand the changes to ISO/IEC 27001:2022 standards and ISO/IEC 27002:2022 standards.
4.2.4.2 除4.2.4.1外,审核组整体应具有ISO/IEC 27002:2022所有控制及其实施方面的知识。In addition to 4.2.4.1, the audit team as a whole should have knowledge of all controls and their implementation in ISO/IEC 27002:2022.
5认证过程管理Certification process management
5. 1询问和申请Inquiry and Application
5. 1. 1 应向申请认证的组织提供公开文件,公开文件的内容应包括以下信息:认证范 围、认证工作程序、认证依据、证书有效期、认证收费标准等。同时应告知申请组织:只有当其已按相应标准建立了管理体系并正常运行三个月以上、至少完成一次内审、管理评审后,BOHAN方可安排现场审核。
Public documents shall be provided to the organization applying for certification, and the contents of the public documents shall include the following information: certification scope, certification work procedures, certification basis, certificate validity period, certification fee standard, etc. At the same time, the applicant organization shall be informed of:BOHAN can arrange on-site audit only after it has established the management system according to the corresponding standards and has operated normally for more than three months and has completed at least one internal audit and management review.
5. 1. 2 申请组织的授权代表签署《认证申请书》,并至少提供以下必要的申请信息:
The authorized representative of the application organization shall sign the application for certification and provide at least the following necessary application information:
(1)申请认证的组织名称、注册地址、经营地址、通讯地址及邮编、联系人、职务、联系方式;
Name, registered address, business address, correspondence address and postcode, contact person, position and contact information of the organization applying for certification;
(2)认证类型;
Type of certification;
(3)认证依据;
Certification basis;
(4)体系覆盖的人数;
The number of people covered by the system;
(5)根据业务、组织、位置、资产和技术等方面的特性所确定的ISMS的范围和边界,包括对任何范围、删减的详细说明和正当性理由;
The scope and boundary of ISMS determined according to the characteristics of business, organization, location, assets and technology, including detailed description of any scope, deletion and justification;
(6)经营场所、分场所、临时场所以及各场所从事的活动等;
Business places, sub venues, temporary places and activities in various places, etc;
(7)服务器数量、终端数量、用户的数量;
The number of servers, terminals and users;
(8)适用性声明、资产列表;
Applicability statement, asset list;
(9)保密协议、信息安全敏感区域的声明;
Confidentiality agreement, declaration of information security sensitive area;
(10)提供咨询服务机构和人员信息;
Providing information services and advisory services;
(11) 申请组织对BOHAN的资质、诚信守法记录或认证人员身份背影的要求以及适用的、最新的与保守国家秘密或维护国家安全有的法律法规要求,以便BOHAN判断是否具备为申请组织实施认证活动的资格或条件;
The requirements of the application organization on BOHAN's qualification, integrity and law-abiding records or the identity of certification personnel, as well as the applicable and latest laws and regulations related to the protection of state secrets or the maintenance of national security, so that BOHAN can judge whether it has the qualification or conditions for implementing certification activities for the application organization;
(12)关于认证活动的限制条件(如出于安全和/或保密等原因,存在时)。
Restrictions on certification activities (e. g. when they exist for security and / or confidentiality reasons).
5. 1. 3申请组织还提供以下资料:
The applicant organization shall also provide the following information:
(1)法人资格证明(工商营业执照、事业单位法人证书或社会团体法人登记证书);
Certificate of legal person qualification (business license for Industry and commerce, certificate of legal person of public institution or registration certificate of legal person of social organization);
(2)取得相关法规规定的行政许可文件(适用时);
Obtain the administrative license documents stipulated by relevant laws and regulations (when applicable);
(3)满足工信部联(2010)394号文《关于加强信息安全管理体系安全管理的通知》以及有关主管部门/监管部门对信息安全管理体系认证的管理要求的证据;
Evidence of meeting the requirements of the Ministry of industry and information technology (2010) No. 394 on strengthening the security management of information security management system and the management requirements of relevant competent departments / regulatory departments for information security management system certification;
(4)手册及相关体系文件;如涉及ISO/IEC 27001:2022标准的换版时,应提交按ISO/IEC 27001:2022标准要求运行三个月后的体系文件及更新后的适用性声明(SOA)。
Manual and related system documents; If a version change of the ISO/IEC 27001:2022 standard is involved, the system documents and updated Statement of Applicability (SOA) after three months of operation in accordance with the requirements of the ISO/IEC 27001:2022 standard should be submitted.
(5)支持ISMS的规程和控制措施、风险评估方法的描述、风险评估报告、风险处置计划、组织为确保其信息安全过程的有效规范/运行和控制以及描述如何测量控制措施的有效性的文件。
Documents supporting ISMS procedures and control measures, description of risk assessment method, risk assessment report, risk disposal plan, organization's effective specification / operation and control of its information security process, and documents describing how to measure the effectiveness of control measures.
5. 2申请评审Application review
5. 2. 1 合同评审人员按照《认证审核管理程序》的规定进行评审以确保:
The contract reviewers shall review according to the provisions of certification audit management procedure to ensure that:
(1)识别申请组织的行业类别和与之相应的信息安全管理过程的特性和服务要求;
Identify the industry category of the application organization and the characteristics and service requirements of the corresponding information security management process;
(2)掌握国家对相应行业的信息安全管理体系认证的管理要求;
Master the national management requirements for information security management system certification of corresponding industries;
(3) 组织根据业务、组织、位置、资产和技术等方面的特性,确定ISMS的范围和边界, 包括对任何范围不适用的详细说明和正当性理由;
The organization determines the scope and boundaries of an ISMS based on the
characteristics of its business, organization, location, assets, and technology, including a detailed explanation and justification for any inapplicability to the scope;
(4)申请组织ISMS范围不允许BOHAN接触的信息资产已明确告知了BOHAN;或者已将BOHAN接触这些信息资产应满足的法律要求、相关方要求及申请组织的要求等明确告知BOHAN;
BOHAN has been informed of the information assets not allowed to be contacted by BOHAN within the scope of ISMS of the application organization; Or it has clearly informed BOHAN of the legal requirements, requirements of related parties and requirements of the application organization that BOHAN should meet when contacting these information assets;
(5)认证要求已有明确说明并形成文件,且已提供给申请组织;
The certification requirements have been clearly stated and documented, and have been provided to the application organization;
(6)解决了BOHAN与申请组织之间任何已知的理解差异;
Any known differences in understanding between BOHAN and the applicant organization have been resolved;
(7)已根据特定的申请组织的具体情况分析对其实施审核和认证所需的能力,BOHAN有能力实施认证活动;
According to the specific situation of the specific application organization, BOHAN has the ability to implement the certification activities;
(8)保持了决定实施审核的理由的记录。
Records of the reasons for the decision to implement the audit are maintained.
5. 2. 2认证证书转换Conversion of certification certificate
带认可标志的信息安全管理体系认证证书可进行转换,转换程序依据《认证证书转换
管理程序》中关于认证证书转换的相关规定执行。
The certification certificate of information security management system with recognition mark can be converted, and the conversion procedure shall be implemented according to the relevant provisions on certification certificate conversion in Procedure for Administration of Certificate Transfer.
5. 2. 3对申请不通过的合同,由市场代表与合同递交部门或申请方联系,洽谈澄清有关事实,取得一致意见后再次评审。如因其他原因构成不能受理的,则向申请方说明情况,发出《不予受理通知书》,按申请方要求退回有关资料。拒绝申请的原因应记录并使客户清楚。
If the contract is not agreed with the contract department, it shall be submitted to the representative of the market for clarification. If the case cannot be accepted due to other reasons, it shall explain the situation to the applicant, issue the "Notice of rejection" and return the relevant information as required by the applicant. The reasons for rejecting the application should be recorded and made clear to the customer.
5. 2. 4 合同的签订和管理程序参照《认证审核管理程序》中的相关规定。
The contract signing and management procedures shall refer to the relevant provisions in the certification and audit management procedures.
5. 3审核方案的策划Planning of Audit Scheme
5. 3. 1总要求General requirements
5. 3. 1. 1审核方案策划人员应根据申请评审的结果,按照《审核方案策划管理办法》的过程要求进行审核方案策划,并将审核方案策划结果传递到审核组,由审核组在现场确认,必要时根据审核组在现场确认的结果调整审核方案。
The planning personnel of the audit scheme shall plan the audit scheme according to the results of the application and in accordance with the process requirements of the management measures for audit scheme planning, and transmit the planning results of the audit scheme to the audit team for confirmation on site. If necessary, the audit scheme shall be adjusted according to the results confirmed by the audit group on site.
5. 3. 1. 2根据申请评审时已识别的特定的申请组织的具体情况分析对其实施审核和认 证所需的能力,委派具备相应能力的审核组实施审核。当了解到特定的获证组织的ISMS已发生变化时(特别是在监督审核、再认证审核方案策划时),审核方案管理人员应对原有的能力分析进行审查,必要时进行更新,并按更新后的能力需求委派具备相应能力的审核组实施审核,确保审核的有效性。
According to the specific situation of the specific application Organization identified during the application review, analyze the ability required for its implementation of audit and certification, and appoint an audit team with corresponding ability to carry out audit. When it is known that the ISMS of a specific certified organization has changed (especially in the planning of supervision audit and recertification audit scheme), the, The audit scheme manager shall review the original capability analysis, update it if necessary, and appoint an audit team with corresponding ability to audit according to the updated capacity requirements to ensure the effectiveness of the audit.
5. 3. 1. 3审核时间的策划按要求策划每个申请ISMS认证的组织的初次审核(含一、二阶段)、监督审核及再认证审核所需的审核时间。初次认证审核分为第一阶段和第二阶段。确定受审核组织的审核时间时,应考虑组织的 ISMS范围所涉及的服务活动种类、 组织规模及业务的复杂程度等因素对核定审核活动所需的审核时间的影响。 安排审核时间应考虑一下因素:
Audit time planning the audit time required for the initial audit (including stage I and II), supervision audit and recertification audit of each organization applying for ISMS certification. The initial certification audit is divided into the first stage and the second stage. When determining the audit time of the audited organization, The influence of the type of service activities involved in the scope of ISMS, the size of the organization and the complexity of the business on the audit time required for the audit activities should be considered. The following factors should be taken into account when arranging the audit time:
a)ISMS范围的规模(例如,所使用的信息系统的数量和雇员的数量);
The scale of the scope of the ISMS (e. g. , the number of information systems used and the number of employees); and;
b)ISMS的复杂程度(例如,信息系统的关键程度和ISMS的风险状况);
b)The complexity of the ISMS (e. g. , the criticality of the information system and the risk profile of the ISMS);
c)在 ISMS范围内开展的业务类型;
c) The type of business carried out within the scope of ISMS;
d)在 ISMS各部分的实施过程中,所应用的技术的水平和多样性[例如,已实施的控制 措施、文件和(或)过程控制,以及纠正和(或)预防措施等];
The level and diversity of technologies applied in the implementation of each part of the ISMS [e. g. , control measures implemented, document and / or process control, and corrective and / or preventive measures, etc. )];
e)场所的数量;
The number of sites;
f)经证实的以往ISMS绩效;
Proven past isms performance;
g)在 ISMS范围内,所使用的外包和第三方安排的程度;
The extent of outsourcing and third party arrangements used within the scope of ISMS;
h)适用于认证的标准和法规。
Standards and regulations applicable to certification.
5. 3. 1. 4应考虑受审核组织是否有不允许BOHAN接触的包含保密性/敏感性的信息资产或 BOHAN接触该类信息资产时应满足的特殊要求。同时应对客户不允许或者限制解除的信息资产对审核的影响进行评估并采取相应的措施。
Consideration should be given to whether the audited organization has information assets containing confidentiality / sensitivity that are not allowed to be contacted by BOHAN or the special requirements that BOHAN should meet when contacting such information assets. At the same time, we should evaluate the impact of the information assets that the customer does not allow or limit to remove on the audit and take corresponding measures.
5. 3. 2基准审核时间附录C. 1为初次审核时间,包括第一、第二阶段审核时间的总和。每个组织所需的时间取决于组织规模、复杂程度、审核范围等诸多因素。
Benchmark audit time appendix C. 1 is the initial audit time, including the sum of the first and second stage audit time. It depends on many factors such as the size of the organization, the complexity of the organization, and so on.
5. 3. 3多场所抽样Multi site sampling
(1)抽样的条件
Sampling conditions
当客户组织拥有满足以下条件的多个场所时,适用CNAS-CC11,基于抽样的方法进行多场所抽样审核:
When the customer organization has multiple sites meeting the following conditions, CNAS-CC11 is applicable to conduct multi site sampling audit based on sampling method:
a) 所有的场所在同一ISMS下运行,并接受统一的管理、内部审核和管理评审;
All sites operate under the same ISMS and receive unified management, internal audit and management review;
b) 所有的场所都包含在客户组织的 ISMS内部审核方案中;
All sites are included in the ISMS internal audit program of the customer organization;
c) 所有的场所都包含在客户组织的 ISMS管理评审方案中。
All sites are included in the customer organization's ISMS management review program.
(2)抽样的考虑
Sampling considerations
a)申请评审管理人员在使用基于抽样的方法时,应确保抽样审核的结果应可以满足证 明其ISMS的适宜性、充分性和有效性,如果抽样无法满足以下要求时应进行相应的调整;
When using the sampling based method, the management personnel of application for review shall ensure that the results of sampling audit can meet the requirements to prove the suitability, sufficiency and effectiveness of ISMS. If the sampling fails to meet the following requirements, corresponding adjustments shall be made;
b)在初次的合同评审中,最大程度地识别场所之间的差异,以便确定适宜的抽样水平 并结合以下因素抽取具有代表性的场所,以体现抽样样本的代表性和随机性:
In the initial contract review, the differences between sites shall be identified to the greatest extent, so as to determine the appropriate sampling level, and representative places shall be selected in combination with the following factors to reflect the representativeness and randomness of the sampling samples:
1)总部及其他场所的内部审核的结果;
Results of internal audit of headquarters and other places;
2)管理评审的结果;
Results of management review;
3)场所规模的异同;
The similarities and differences of site scale;
4)场所业务目的的异同;
The similarities and differences of business purposes of the site;
5)ISMS的复杂程度;
The complexity of ISMS;
6)不同场所的信息系统的复杂程度;
The complexity of information system in different places;
7)工作惯例的异同;
The similarities and differences of work practices;
8)所实施的活动的异同;
The similarities and differences of the activities implemented;
9)与关键的信息系统或处理敏感信息的信息系统之间的潜在相互作用;
Potential interactions with key information systems or information systems dealing with sensitive information;
10)任何不同的法律要求。
Any different legal requirements.
c)从客户组织的 ISMS范围内所有场所中选择具有代表性的样本,这种选择应基于判 断以反映上述 b)中所列因素,同时也考虑随机因素;
In addition, the selection of all the factors mentioned above should be based on the random selection of the customers;
d)在授予认证之前,认证机构审核 ISMS中每个有重大信息安全风险的场所;
Before the certification is granted, the certification authority shall audit each site with significant information security risk in ISMS;
e)根据上述要求,设计审核方案,并在三年的时间内覆盖ISMS认证范围内的代表性 样本;
According to the above requirements, design the audit scheme and cover the representative samples within the scope of ISMS certification within three years;
f)无论是在总部还是在某单一场所发现不符合,纠正措施规程的实施适用于包括在认证范围内的总部和所有场所。
The implementation of the corrective action procedure is applicable to the headquarters and all sites within the scope of certification, whether it is found in the headquarters or in a single site.
(3)抽样量在多场所抽样时,初次认证审核抽样样本量通常不低于同种类样本总量的平方根;监督审核抽样样本量通常不低于同种类样本总量平方根的 0. 6倍,再认证审核抽样样本量通常不低于同种类样本总量平方根的 0. 8倍。
When the sample size is sampled in multiple places, the sample size of the initial certification audit is usually no less than the square root of the total number of samples of the same type; The sample size of supervision audit is usually no less than 0. 6 times of the total square root of the same kind of sample, and the sample size of re certification audit is not less than 0. 8 times of the total square root of the same kind of sample.
5. 3. 4初次审核在基准审核时间(附录C. 1)的基础上,对申请组织提供的申请材料,考虑增减因素后确定适宜的初次审核时间。ISMS第一阶段审核应安排在受审核组织的现场进行,审核时间不宜少于0. 5个审核人日,当客户组织由于信息安全的原因在申请评审阶段不能提供足够的信息时,应增加第一阶段现场审核时间。
On the basis of the benchmark audit time (Appendix C. 1), the appropriate initial audit time shall be determined after considering the increase and decrease factors for the application materials provided by the application organization. The first stage audit of ISMS shall be arranged at the site of the audited organization, and the audit time shall not be less than 0. 5 auditor days, When the customer organization can not provide enough information in the application review stage due to information security reasons, the first stage of on-site audit time should be increased.
5. 3. 5监督审核及再认证
Supervision, audit and recertification
5. 3. 5. 1审核时间如果没有重大变化影响到审核时间调整,对获证组织的监督审核的时间安排宜与初次认证审核审核时间成比例,每年用于监督审核的时间总量应不低于初次认证审核审核总时间的三分之一,再认证审核的时间总量应不低于初次认证审核审核总时间的三分之二。BOHAN将适时地核查其监督审核及再认证审核时间策划的合理性,确认监督审核方 案策划及再认证审核策划是否考虑客户组织的变更及 ISMS的成熟度等因素的影响,必要时对监督审核审核或再认证审核时间予以调整以确保审核的结果足以证实获证组织ISMS的适宜性、充分性和有效性。
If there is no significant change in the audit time that affects the adjustment of the audit time, the time arrangement for the supervision and audit of the certificated organization should be proportional to the audit time of the initial certification audit, and the total amount of time used for supervision and audit each year shall not be less than one third of the total audit time of the initial certification, The total time of re certification audit shall not be less than two thirds of the total time of initial certification audit. BOHAN will timely check the rationality of its supervision audit and recertification audit time planning, and confirm whether the supervision and audit plan and re certification audit plan consider the influence of customer organization changes and ISMS maturity, When necessary, the time of supervision audit or recertification audit shall be adjusted to ensure that the audit results are sufficient to confirm the suitability, adequacy and effectiveness of ISMS of the certified organization.
5.3.5.2 ISO/IEC 27001:2022 标准转换审核时间ISO/IEC 27001:2022 standard conversion review time
当再认证进行转换时,在规定的审核人日基础上转换可依据组织的规模/复杂程度/受法规管制的程度/过程风险等因素增加不低于0.5人日的审核时间,以确保ISO/IEC 27001:2022标准转换审核的有效性。对于结合监督或单独开展转换审核的,根据组织的自身具体情况为转换审核确定充分的审核时间,以确保组织满足ISO/IEC 27001:2022标准的全部要求,所确定的转换审核时间不应少于1人天。
When conducting a conversion in combination with supervision and recertification, the conversion can increase the audit time by no less than 0.5 person days based on factors such as the size/complexity/degree of regulatory control/process risk of the organization, to ensure the effectiveness of the ISO/IEC 27001:2022 standard conversion audit. For conversion audits conducted separately, sufficient audit time should be determined for the conversion audit based on the specific situation of the organization to ensure that the organization meets all requirements of ISO/IEC 27001:2022 standards. The determined conversion audit time should not be less than 1 person day.
5. 3. 5. 3审核关注点的策划Planning of audit concerns
(1)内审、管理评审和预防措施、纠正措施的实施情况;
Implementation of internal audit, management review and preventive and corrective measures;
(2)针对上次评审的不符合所采取的措施的有效性;
Effectiveness of the measures taken for the non conformity of the last review;
(3)根据ISMS标准及认证其他文件要求,与外部各方的沟通情况;
Communicate with external parties according to ISMS standards and other certification documents;
(4)文件化管理体系的变更及涉及变更的区域;
Changes to the documented management system and the areas involved in the changes;
(5)针对获证组织与信息安全有关的资产威胁、脆弱性和影响的评估、控制措施的选择及对控制措施有效性的监视测量。
The assessment of the threat, vulnerability and impact of the certified organization's assets related to information security, the selection of control measures and the monitoring and measurement of the effectiveness of the control measures.
5. 3. 5. 4监督审核频次在满足认可要求的基础上,根据获证组织信息安全管理体系覆盖的业务活动的特点以及所承担的风险,合理设计和确定监督审核的时间间隔和频次。当获证组织信息安全管理体系发生重大变更,或发生重大问题、服务质量事故、客户投诉等情况时,应视情况可增加监督的频次。监督审核的最长时间间隔不超过12个月。由于获证组织业务 运作的时间(季节)特点及其内部审核安排等原因,可以合理选取和安排监督周期及时机,监督审核必须覆盖信息安全管理体系认证范围内的所有业务活动。
The time and frequency of the audit activities, and the frequency of the audit activities to meet the requirements of the safety management system. When the certified organization's information security management system changes significantly, Or in case of major problems, service quality accidents, customer complaints, etc. , the frequency of supervision shall be increased according to the situation. The longest time interval of supervision and audit shall not exceed 12 months. Due to the time (season) characteristics of the certified organization's business operation and its internal audit arrangement, the supervision cycle and timely time can be reasonably selected and arranged, The supervision and audit must cover all business activities within the scope of information security management system certification.
5. 3. 5. 5如果在监督或再认证审核中, 发现不符合存在,该不符合在认证机构同意的时间内应得到有效的纠正。如果纠正没有在同意的时间内完成,认证范围应被缩小,或者暂停或撤销认证证书。允许采取纠正措施的时间应与不符合的严重程度和风险相适宜,以 确保客户组织的产品或服务满足规定要求。
If a non-conformance is found during the supervision or re certification audit, the non-conformance shall be effectively corrected within the time agreed by the certification body. If the correction is not completed within the agreed time, the scope of certification should be reduced, or the certification certificate should be suspended or revoked. The time allowed for corrective action should be appropriate to the severity and risk of the nonconformity to ensure that the customer organization's products or services meet specified requirements.
5. 3. 6选择和指派审核组审核方案管理人员应根据实现审核目标所需的能力来选择和任命审核组(包括审核组长),应确保他们是经过BOHAN的审核能力和专业能力评定、有能力完成本次审核任务的 人员。如果仅有一名审核员,该审核员应有能力履行适用于该审核的审核组长职责。决定审核组的规模和组成时,应考虑下列因素: 审核组必须拥有审核范围内的所有技术领域(附录A)对应的能力。应有能审核受审核组织认证范围的专业审核员,否则应在技术专家支持下实施审核。审核组长和审核员所需的知识和技能可以通过技术专家和翻译人员补充,技术专家和翻译人员应在审核员的指导下工作。使用翻译人员时,要避免其对审核产生不正当影响。每次审核(包括一阶段和二阶段审核)的审核组均应具备专业能力。
Select and assign the audit team. The audit scheme management personnel shall select and appoint the audit team (including the audit team leader) according to the ability required to achieve the audit objectives, and ensure that they are the personnel who have passed the evaluation of Bohan's audit ability and professional ability and are capable of completing the audit task. If there is only one auditor, the auditor shall be able to perform the duties of audit team leader applicable to the audit. When determining the size and composition of the audit team, the following factors shall be considered: the audit team must have the corresponding capabilities in all technical fields within the audit scope (Appendix A). There should be professional auditors who can audit the certification scope of the audited organization, otherwise the audit should be carried out with the support of technical experts. The knowledge and skills required by the audit team leader and auditors can be supplemented by technical experts and translators, who shall work under the guidance of auditors. When using translators, it is necessary to avoid their improper influence on the audit. The audit team of each audit (including phase I and phase II audit) shall have professional competence.
5. 4审核的实施要求Implementation audit
5. 4. 1保密管理要求在现场审核中的落实
Implementation of confidentiality management requirements in site audit
5. 4. 1. 1审核组在审核现场发现存在任一情况时应立即向公司汇报,并按公司所确定的 相应措施完成后续工作: (1)如果发现受审核组织不允许接触信息资产或无法满足受审核组织关于接触信息资产的相关要 求时,BOHAN对审核和认证所受到的影响进行评估并采取相应措施(例如终止审核、缩小审核和认证的范围等);(2)如果受审核组织事先没有禁止BOHAN接触某一信息资产或未和告知BOHAN关于接触信息资产的相关要求,而BOHAN在认证过程中发现自己不具备接触该信息资产的资格和条件时,应立即向受审核组织提出。
The audit team shall report to the company immediately when any situation is found on the audit site, and complete the follow-up work according to the corresponding measures determined by the company: (1) if it is found that the audited organization is not allowed to access information assets or cannot meet the relevant requirements of the audited organization on access to information assets When required, BOHAN evaluates the impact of audit and certification and takes corresponding measures (such as terminating audit, reducing the scope of audit and certification, etc. ); (2) If the audited organization has not prohibited BOHAN from contacting an information asset or has not informed BOHAN of relevant requirements for access to information assets in advance, However, when BOHAN finds out that he / she does not have the qualification and conditions to contact the information assets during the certification process, he / she shall immediately submit it to the audited organization.
5. 4. 1. 2审核组成员不宜在审核过程中以任何方式记录受审核组织的保密或敏感信息; 在离开受审核组织前,应请受审核组织检查和确认审核组携带的文件、资料和设备中未夹带受审核组织的任何保密或敏感信息。
Members of the audit team should not record the confidential or sensitive information of the audited organization in any way during the audit process; Before leaving the audited organization, the audited organization shall be asked to check and confirm that the documents, materials and equipment carried by the audit team do not contain any confidential or sensitive information of the audited organization.
5. 4. 2审核方法Audit method
5. 4. 2. 1信息收集方法应包括(但不限于):
Information collection methods shall include (but not limited to) the following:
(1)面谈;
Interview;
(2)对过程和活动进行观察;
Observe the process and activities;
(3)审查文件和记录。
Review documents and records.
5. 4. 2. 2如果在审核中使用远程审核技术,审核组在审核计划中应具体说明。
If remote audit technology is used in the audit, the audit team shall specify it in the audit plan.
5.4.3 初次认证审核 Initial audit
通用要求执行《认证审核管理程序》的要求。The general requirement is to implement the
requirements of the Certification Audit Management Procedure.
5.4.3.1一阶段审核Stage 1 audit
5.4.3.1.1在该审核阶段,审核员应获取有关ISMS设计的文件,其中包括ISO/IEC 27001所要求的文件。
During this audit phase, the auditor should obtain documents related to ISMS design, including those required by ISO/IEC 27001..
5. 4. 3. 1.2审核员应充分了解在组织环境下所进行的ISMS设计、风险评估和处置(包括所确定的控制)、信息安全方针和目标,以及特别是客户的审核准备情况。
Auditors should have a thorough understanding under the control of organizational environment of the ISMS design, risk assessment and disposal (including identified controls), information security policies and objectives ,and especially the client's audit preparation status.
5.4.3.1.3 第一阶段的结果应形成书面报告。在决定进行第二阶段之前,技委会应审查第一阶段的审核报告,以便为第二阶段选择具有所需能力的审核组成员;如果认为胜任和合适,可由领导第一阶段审核的审核员完成。
The results of stage 1 shall be documented in a written report. The certification body shall review the stage 1 audit report before deciding on proceeding with stage 2 and shall confirm if the stage 2 audit team members have the necessary competence; this may be done by the auditor leading the team that conducted the stage 1 audit if deemed competent and appropriate.
5.4.3.1.4 审核组应让客户知晓第二阶段可以要求对更进一步的信息和记录做详细检查。The audit team should inform customers that the second stage can require a detailed inspection of further information and records.
5. 4. 3.2二阶段审核Stage 2 audit
基于第一阶段审核报告中的审核发现,审核组长制定实施第二阶段的审核计划。除了评价ISMS的有效实施之外,第二阶段的目的是:确认客户遵守自身的方针、策略和规程。
Based on the audit findings in the stage 1 audit report, the audit team leader develops stage 2 audit plan. In addition to evaluating the effective implementation of ISMS, the purpose of the stage 2 is to confirm that customers comply with their own policies, strategies, and procedures.
5. 4. 3.2.1二阶段审核应重点关注申请组织的下列方面:
The Stage 2 audit shall focus on the following aspects of the application organization:
(1) 最高管理者的领导力和对信息安全方针与信息安全目标的承诺;
Leadership of top management and commitment to information security policies and objectives;
(2) ISO/IEC 27001 中所列的文件要求;
The document requirements listed in ISO/IEC 27001;
(3) 评估与信息安全有关的风险,以及评估可产生一致的、有效的、在重复评估时可比较的结果;
Assess the risks related to information security, and assess whether the assessment can produce consistent, effective, and comparable results when repeated;
(4) 基于风险评估和风险处置过程,确定控制目标和控制;
Based on risk assessment and risk disposal process, determine control objectives and controls;
(5) 信息安全绩效和ISMS有效性,以及根据信息安全目标对其进行评审;
Information security performance and ISMS effectiveness, as well as their evaluation based on information security objectives;
(6) 所确定的控制、适用性声明、风险评估与风险处置过程的结果、信息安全方针与目标,它们相互之间的一致性;
The consistency between the identified controls, applicability statements, results of risk assessment and disposal processes, information security policies and objectives, and their interrelationships;
(7) 控制的实施,考虑了外部环境、内部环境与相关的风险,以及组织对信息安全过程和控制的监视、测量与分析,以确定控制是否得以实施、有效并达到其所规定的目标;
Implementation of control,considering the external environment, internal environment, and related risks, as well as the organization's monitoring, measurement, and analysis of information security processes and controls, to determine whether the controls are implemented, effective, and achieve their specified goals;
(8) 方案、过程、规程、记录、内部审核和对 ISMS有效性的评审,以确保其可被追溯 至管理决定和ISMS方针与目标;
Plan, process, procedure, record, internal audit and review of ISMS effectiveness to ensure that they can be traced back to management decisions and ISMS policies and objectives;
5. 4. 3.2. 2对受审核组织的ISMS范围和边界的界定的充分性和合理性应在第二阶段审核报告中予以描述。
The sufficiency and rationality of the definition of the scope and boundary of ISMS of the audited organization shall be described in the second stage audit report.
5. 4. 4 监督审核执行《认证审核管理程序》的要求。
Surveillance audits should comply with the requirements of the Certification Audit Management Procedure.
5.4.4.1 监督审核程序,应与本文件中有关客户ISMS的认证审核的要求和指南保持一致。The surveillance audit procedure should be consistent with the requirements and guidelines for the certification audit of customer ISMS in this document.
监督的目的是验证已被认证的ISMS得到持续实施、考虑客户运作变化所引起的管理 体系变化的影响并确认与认证要求的持续符合。监督审核方案应至少包括The purpose of surveillance is to verify the continuous implementation of certified ISMS, consider the impact of management system changes caused by changes in customer operations, and confirm continuous compliance with certification requirements. The surveillance audit program should at least include:
a)管理体系的保持要素,如信息安全风险评估与控制的维护、ISMS内部审核、管
理评审和纠正措施;The maintenance elements of the management system, such as information security risk assessment and control maintenance, ISMS internal audits, management reviews, and corrective measures;
b)根据ISMS标准ISO/IEC 27001和认证所需的其他文件的要求,与来自外部各方
沟通;Communicate with external parties in accordance with the requirements of the ISMS standard ISO/IEC 27001 and other documents required for certification;
c)文件化管理体系的变更;Changes to the documented management system;
d)发生变更的区域;The area where the change occurred;
e)所选择的ISO/IEC 27001的要求;The requirements of the selected ISO/IEC 27001;
f)适宜时,其他所选择的区域。When appropriate, other selected areas.
5. 4. 4. 2监督审核应包括(但不限于)以下内容:
Surveillance audit shall include (but not limited to) the following contents:
(1) ISMS 在实现客户信息安全方针的目标方面的有效性;The effectiveness of ISMS in achieving the goals of customer information security policy;
(2) 对与相关信息安全法律法规的符合性进行定期评价与评审的规程的运行情况;The operation status of the regulations for regular evaluation and review of compliance with relevant information security laws and regulations;
(3) 所确定的控制的变更,及其引起的SoA的变更;The identified changes in control and the resulting changes in SoA;
(4) 控制的实施和有效性(根据审核方案来审查);The implementation and effectiveness of control (reviewed according to the audit plan);
(5) 顾客投诉情况;Client complaints;
(6) 涉及变更的范围;The scope of changes involved;
(7) 内部审核与管理评审;Internal audit and management review;
(8) 对上次审核时提出的不符合所采取纠正措施的审查;Review of corrective measures taken for non conformities identified during the last audit;
(9) 标志的使用和(或)任何其他对认证资格的引用;The use of the logo and/or any other reference to the certification qualification;
(10) 适当时,其它选定的范围。When appropriate, other selected ranges.
5.4.4.3 应能够针对与信息安全问题相关的风险及其对客户的影响来调整监督方案,并说明监督方案的合理性。We should be able to adjust the supervision plan based on the risks related to information security issues and their impact on customers, and explain the rationality of the surveillance plan.
5.4.4.4 监督审核可以与其他管理体系的审核相结合。报告应清晰地指出与每个管理体系相关的方面。 Surveillance audits can be combined with audits of other management systems. The report should clearly indicate the aspects related to each management system.
5.4.4.5 在监督审核过程中,审核组应检查客户提交给认证机构的申诉和投诉记录,并且在发现任何不符合或不满足认证要求时,还应检查客户是否对其自身的ISMS和规程进行了调查并采取了适当的纠正措施。 During the surveillance and audit process, the audit team should check the appeals and complaint records submitted by customers to the certification body, and when any non-compliance or non-compliance with certification requirements is found, it should also check whether the customer has investigated their own ISMS and procedures and taken appropriate corrective measures.
5.4.4.6监督报告应包括有关消除以往出现的不符合、SoA版本和从上次审核之后发生的重大变更的信息。监督审核报告应至少完全覆盖本文件的5.4.10.2和5.4.10.3 的要求。
The surveillance report should include information on eliminating past non conformities, SoA versions, and significant changes that have occurred since the last audit. The supervisory audit report should at least fully cover the requirements of 5.4.10.2 and 5.4.10.3 of this document.
5. 4. 5再认证审核执行《认证审核管理程序》,审核内容同初次认证审核。
The recertification audit shall be conducted in accordance with the certification audit management procedure. The audit content is the same as the initial certification audit
5. 4. 6特殊审核特殊审核,包括扩大认证范围的审核、提前较短时间通知的审核(含投诉调查、认证范围变更、暂停恢复等),执行《授予、保持、更新、扩大、缩小、暂停和撤销认证的管理程序》的规定。
Special audit special audit, including the audit of expanding the scope of certification and the audit with short notice in advance (including complaint investigation, change of certification scope, suspension and resumption, etc. ) shall be implemented in accordance with the provisions of management procedures for granting, maintaining, updating, expanding, narrowing, suspending and revoking certification.
5.4.7 ISO/IEC 27001:2022 标准换版审核ISO/IEC 27001:2022 standard version change review
审核内容应包括,但不限于The audit content shall include, but not limited to:
1)ISO/IEC 27001:2022的差距分析,以及客户ISMS的变更需求;Gap analysis of ISO/IEC 27001:2022 and customer ISMS change requirements;
2)符合性声明(SOA)的更新;Updates to the Statement of Conformity (SOA);
3)适用时,风险处置计划的更新;Update the risk disposal plan when applicable;
4)客户所选的、新的或变化的信息安全控制的实施情况及其有效性。Implementation and effectiveness of customer selected, new, or changed information security controls.
5. 4. 8远程审核Remote audit
如果拟使用远程审核技术(例如,交互式基于 web 的协作、web会议、电话会议和/ 或组织过程的电子验证),可以考虑将其作为审核时间的一部分。如果审核计划中远程审核活动占据大于30%的现场审核时间。安排远程审核时,BOHAN将确定审核计划的适当性,并在实施前得到认可机构的特殊批准。注:现场审核时间是指单独场所的现场审核时间。远程场所的电子审核被视为远程审核,即使电子审核在组织的物理场所进行。
If it can be considered as part of a web-based audit, a teleconference, and a collaborative process, such as an audit, a teleconference, and a collaborative process to be considered. If the remote audit activities in the audit plan occupy more than 30% of the on-site audit time. When scheduling a remote audit, BOHAN will determine the appropriateness of the audit plan, And obtain special approval from authorized institutions before implementation. Note: the on-site audit time refers to the on-site audit time of a separate site. Electronic audits at remote locations are considered remote audits, even if they are conducted at the physical site of the organization.
5.4.9 ISMS审核的特定要素Specific elements of ISMS audit
审核组应The audit team should:
a)要求客户证实对信息安全相关风险的评估与ISMS范围内的ISMS运行是相关的和 充分的;Require customers to confirm that the assessment of information security related risks is relevant and sufficient for the operation of ISMS within the scope of ISMS;
b)确定客户识别、检查和评价信息安全相关风险的规程及其实施结果是否与客户的方针、目标和指标相一致;Determine whether the procedures for identifying, inspecting, and evaluating information security related risks for customers and their implementation results are consistent with the customer's policies, goals, and indicators;
c)确定用于风险评估的规程是否健全并得到正确实施。Determine whether the procedures used for risk assessment are sound and properly implemented.
5. 4. 10审核报告审核报告编制的基本要求参照《认证审核管理程序》。
The basic requirements for the preparation of audit report shall refer to certification audit management procedure.
5. 4. 10. 1报告程序应确保:
The reporting procedure shall ensure that:
(1) 在离开客户组织场所前,在审核组和客户组织管理者之间召开一次会议,并提供:
Before leaving the customer organization site, hold a meeting between the audit team and the customer organization manager, and provide:
a)ISMS与特定认证要求的符合性方面的书面或口头说明;
Written or oral explanation on the compliance of ISMS with specific certification requirements;
b)客户组织就审核发现及其根据提出问题的机会。
Opportunities for customer organizations to raise questions about audit findings and their basis.
(2)审核组向认证机构提供关于审核发现的审核报告,这些审核发现是针对客户组织的ISMS与所有认证要求的符合性。
The audit team provides the certification body with audit reports on the conformity of the customer organization's ISMS with all certification requirements.
5. 4. 10. 2审核报告应提供以下信息或对这些信息的引用:
The audit report shall provide the following information or reference to such information:
(1)审核的说明,其中包括了文件评审摘要;
Description of the audit, including the summary of document review;
(2)对客户组织信息安全风险分析进行的认证审核的说明;
A description of the certification audit for the information security risk analysis of the customer organization;
(3)所使用的全部审核时间和分别用于文件评审、风险分析的评审、现场审核和审核报告的时间的详细说明;
A detailed description of the total audit time used and the time used for document review, risk analysis review, site audit and audit report respectively;
(4)所进行的审核询问,及其选择的理由和所使用的方法。
The audit inquiry conducted, the reasons for its selection and the method used.
5. 4. 10. 3审核报告应足够详细,以帮助和支持认证决定。审核报告应包括:
The audit report should be sufficiently detailed to support the decision. The audit report shall include:
(1) 审核覆盖的区域(例如,认证要求和接受审核的场所),也包括所采用的主要审核路线和所使用的审核方法(见本文件的6. 4. 2);
The areas covered by the audit (e. g. certification requirements and audit sites) also include the main audit routes adopted and the audit methods used (see 6. 4. 2 of this document);
(2) 观察结果,包括正面的(例如,值得注意的特点)和负面的(例如,潜在的不符合);
Observations, including positive (e. g. , noteworthy features) and negative (e. g. , potential non-compliance); and;
(3) 已识别的任何不符合的详细情况,包括支持它们的客观证据和这些不符合或认证所需的其他文件的要求;
Details of any non conformity identified, including the objective evidence supporting them and the requirements of ther documents required for certification involved in the non conformity;
(4)有关客户组织的 ISMS与认证要求的符合性方面的意见和对不符合的清楚说明,所引用的适用性声明的版本,以及适用时,与客户组织先前的认证审核结果的任何有用的对照。 完成的问卷、检查清单、观察结果、日志或审核员笔记可能构成完整的审核报告的一部分。如果使用这些方法,这些文件应提供给认证机构,以此作为支持认证决定的证据。在审核过程中,有关被评价样本的信息应包含在审核报告或其他认证资料中。
Comments on the compliance of the customer organization's ISMS with the certification requirements and a clear description of the non-compliance, the version of the statement of applicability cited, and, where applicable, any useful comparison with the results of previous certification audits of the customer organization. Completed questionnaires, checklists, observations, logs or auditor's notes may form part of a complete audit report. If these methods are used, these documents shall be provided to the certification body as evidence to support the certification decision. During the audit process, the information about the evaluated samples should be included in the audit report or other certification materials.
报告应考虑客户组织所采用的内部组织和规程的充分性,以便对其ISMS建立信心。 除了在《认证审核管理程序》中对审核报告的要求,报告还应包括:
The report should take into account the adequacy of the internal organization and procedures adopted by the customer organization in order to build confidence in its ISMS. In addition to the requirements of audit report in certification audit management procedure, the report shall also include:
a)对ISMS内部审核和管理评审的信任程度;
The degree of trust in internal audit and management review of ISMS;
b)有关ISMS要求和信息安全控制的实施和有效性的最重要的正面与负面观察的摘要;
Summary of the most important positive and negative observations regarding the implementation and effectiveness of ISMS requirements and information security controls;
c)审核组关于是否授予客户组织 ISMS认证的建议,以及支持该建议的信息。
Suggestions from the audit team on whether to grant ISMS certification to the client organization, as well as information supporting this suggestion.
5. 5认证决定Certification decision
认证决定工作执行《认证决定管理程序》的要求,应基于审核报告中审核组对客户ISMS是否通过认证的建议。The certification decision work shall comply with the requirements of the Certification Decision Management Procedure, and shall be based on the recommendations of the audit team in the audit report on whether the customer's ISMS has passed certification.
5. 5. 1当了解到特定的获证组织的ISMS已发生变化时(特别是在监督审核、再认证审核方案策划时),并已对原有的能力分析评价后进行更新,应按更新后的能力需求委派具备相应能力的认证决定人员完成认证评定,确保认证决定的有效性。
When it is known that the ISMS of a specific certified organization has changed (especially in the planning of supervision audit and re certification audit scheme), and the original ability analysis and evaluation has been updated, the certification decision-maker with corresponding ability shall be appointed to complete the certification evaluation according to the updated ability requirements, so as to ensure the effectiveness of the certification decision.
5. 5. 2关注信息安全有关的资产、威胁、脆弱性的识别情况、信息安全风险评估、风险 处置及其相应的控制措施的有效性。
Pay attention to the identification of information security related assets, threats and vulnerabilities, information security risk assessment, risk disposal and the effectiveness of corresponding control measures.
5.5.3 通常情况下,对授予认证做出决定的人员或委员会不宜推翻审核组的负面建议。如 果发生这种情况,技委会应记录其作出推翻建议的决定的依据,并说明其合理性。In general, it is not advisable for the personnel or committee making the decision on granting certification to overturn the negative recommendations of the audit team. If such a situation occurs, the Technical Committee should record the basis for its decision to overturn the proposal and explain its reasonableness.
5.5.4 只有具备充分的证据证实管理评审和 ISMS 内部审核的安排已经实施,且是有效的并将得到保持,才可向客户授予认证。Certification can only be granted to clients if there is sufficient evidence to prove that the arrangements for management reviews and internal ISMS audits have been implemented, are effective, and will be maintained.
5. 6认证范围的界定
Definition of certification scope
5. 6. 1总则应根据其业务、组织、技术、物理和资产的特性充分、清晰地界定了其ISMS的范围和 边界。受审核组织的信息安全风险评估和风险处置与其 ISMS 的范围和边界一致,并其适用性声明中得到体现;与不完全属于客户组织ISMS范围内的服务或活动的接口已得到说明,并已包括在客户组织的信息安全风险评估中,例如:与其他机构共享设施的情况(信息技术系统、数据库和通讯系统等)。
The scope and boundary of ISMS shall be fully and clearly defined according to the characteristics of its business, organization, technology, physics and assets. The information security risk assessment and risk disposal of the audited organization are consistent with the scope and boundary of its ISMS, and are reflected in the applicability statement; The interface with services or activities not entirely within the scope of the customer organization's ISMS has been described and included in the customer organization's information security risk assessment, for example, the sharing of facilities with other organizations (information technology systems, databases, communication systems, etc. ).
5. 6. 2业务范围和边界的界定业务范围和边界主要包括关键业务及业务特性描述(业务、服务、资产和每一个资产的责任范围和边界等的说明)。一般从其从事的业务流程进行描述,如软件开发、系统集成等。如果客户组织只是选择其部分业务流程进入到ISMS范围,则必须确保被选择的业务流程所涉及的所有资产均已在风险评估中予以考虑,对于ISMS范围内的业务流程与范围之外的业务流程共用的资产和技术,要识别其可能产生的风险及相应的控 制措施需求。
Definition of business scope and boundary business scope and boundary mainly include description of key business and business characteristics (description of business, service, asset and responsibility scope and boundary of each asset). They are engaged in general software development, such as system integration. If the customer organization only selects part of its business processes to enter the scope of ISMS, It is necessary to ensure that all assets involved in the selected business process have been considered in the risk assessment. For the assets and technologies shared by the business processes within the scope of ISMS and those outside the scope, the possible risks and corresponding control measures need to be identified.
5. 6. 3组织范围和边界的界定
Definition of organizational scope and boundary
组织范围和边界一般可以通过ISMS 范围内的职能部门、过程、组织结构来界定。 对于没有纳入到组织ISMS 范围内的职能和部门,客户组织应提供将其排除在外的适 当理由。在界定组织范围和边界时,宜考虑以下因素:
The scope and boundary of an organization can generally be defined by functional departments, processes and organizational structures within the scope of ISMS. For functions and departments not included in the scope of the organization's ISMS, the customer organization shall provide appropriate reasons for excluding them. The following factors should be considered when defining the scope and boundary of an organization:
(1) 在确定组织范围和边界时需考虑组织 ISMS 的PDCA管理的完整性,确保组织ISMS 的PDCA管理所涉及的所有职能和部门均已纳入管理体系范围。如某客户织申请认证的 业务范围是软件开发,则覆盖的组织范围和边界除了软件开发;
When determining the scope and boundary of the organization, the integrity of PDCA management of ISMS should be considered to ensure that all functions and departments involved in PDCA management of ISMS have been included in the scope of management system. If the business scope of a customer organization applying for certification is software development, the scope and boundary of the organization covered are software development;
(2) 业务职能部门外,其它如涉及该业务的ISMS策划部门、监控和持续改进职能部门也宜纳入到其ISMS范围;
Outside the business function department, other ISMS planning departments, monitoring and continuous improvement departments involved in the business should also be included in the scope of their ISMS;
(3) 信息安全管理委员会/管理机构宜包括与 ISMS直接相关的管理人员;
The information security management committee / authority should include managers directly related to ISMS;
(4) 对 ISMS负责的管理层人员宜是对所覆盖的所有职责领域负有最终责任的人员(即 他们的角色通常是由其在组织中的控制力和职责的范围所决定的);
Management personnel responsible for ISMS should be those who have ultimate responsibility for all areas of responsibility covered (i. e. their roles are usually determined by their control and scope of responsibilities in the organization);
(5) 如果负责管理 ISMS的角色不是高层管理人员,则有必要让一名来自最高管理层组 织高层的发起人作为信息安全利益的代表,并在组织的最高层作为ISMS 的代言人; (6)组织范围和边界的界定方式需要使所有相关资产均被纳入风险评估的考虑之中以识别其风险控制需求。对于组织ISMS范围内的职能部门与体系范围外的职能部门共用 的资产与技术,要识别其可能产生的风险及相应的控制措施需求。 基于以上考虑,在界定组织的边界时,宜识别ISMS所影响的所有人员,并将其包括在 组织的范围内。人员的识别可以与过程和(或)职能部门联系起来。如果组织范围内 的某些过程被外包给第三方,这些依赖关系宜清晰地形成文件。
If the role responsible for managing ISMS is not a senior manager, it is necessary to have an initiator from the top management of the organization as the representative of information security interests and the spokesperson of ISMS at the highest level of the organization; (6) The definition of the scope and boundary of an organization requires that all relevant assets be considered in the risk assessment to identify their risk control needs. For the assets and technologies shared by the functional departments within the scope of ISMS and the functional departments outside the scope of the system, the possible risks and corresponding control measures need to be identified. Based on the above considerations, When defining the boundaries of an organization, all personnel affected by ISMS should be identified and included in the scope of the organization. Personnel identification can be linked to processes and / or functions. If some processes within the organization are outsourced to third parties, these dependencies should be clearly documented.
5. 6. 4确定物理范围和边界
Determination of physical scope and boundary
物理范围和边界一般根据组织业务运营实际使用并控制的地理位置,包括建筑物、场所或设施进行界定。对于跨越物理边界的信息系统,客户组织在确定物理范围和边界时宜以下因素:
Physical scope and boundaries are generally defined according to the geographical location used and controlled by the organization's business operations, including buildings, places or facilities. For information systems that cross physical boundaries, customer organizations should consider the following factors when determining physical boundaries and boundaries:
1)远程设备;
Remote equipment;
2)通过顾客的信息系统以及第三方所提供的服务的接口;
Through the customer's information system and the interface of the service provided by the third party;
3)适用时,适当的接口和服务级别。 在考虑以上因素的基础上,物理范围和边界的描述一般宜包括以下适用的方面:
Appropriate interfaces and service levels, when applicable. On the basis of the above factors, the description of physical scope and boundary should generally include the following applicable aspects:
(1)结合职能部门或过程的物理位置以及组织对其的控制程度,对职能部门或流程进行描述;
Describe the functional department or process according to the physical position of the functional department or process and the control degree of the organization;
(2)在组织信息通信技术边界内的储存或包含信息通信技术硬件或ISMS范围内的数据(如在备份磁带上)的专用设施。 如果这些内容不是由组织自己控制,则应将与第三方之间的依从关系形成文件。在确 定客户组织审核范围时宜考虑其临时场所和异地备份地点的情况。对临时场所一般宜 到现场进行审核,但如能同时满足以下条件则可考虑采用其它非现场方式取证:
A dedicated facility within the boundaries of the organization for storing or containing data within the scope of ICT hardware or ISMS (e. g. , on backup tapes). If these are not controlled by the organization itself, compliance with third parties should be documented. When determining the audit scope of the customer organization, the situation of its temporary site and remote backup location should be considered. Generally, temporary places should be audited on site, but other off-site methods can be considered if the following conditions can be met at the same time:
①客户组织的客户有充分合适的理由(例如:客户组织提供的系统集成或服务项目涉及客户机密信息或项目实施地址距离客户组织较远);
The customer of the customer organization has sufficient and appropriate reasons (for example, the system integration or service project provided by the customer organization involves confidential customer information or the project implementation address is far away from the customer organization);
②客户组织已对临时现场风险进行评估并且该残余风险是可接受的,不是重大风险;
The customer organization has assessed the temporary site risk and the residual risk is acceptable and not a significant risk;
③客户组织已经采取措施对临时现场信息安全风险进行监控或定期检查;
The customer organization has taken measures to monitor or regularly inspect the information security risks on temporary sites;
④审核员确认通过上述方法客户组织的信息安全风险可以得到控制。如果组织内有建筑物、场所或设施没有纳入到ISMS范围内的,客户组织宜说明其排除在外的适当理由。
The auditor confirms that the information security risk of the customer organization can be controlled through the above methods. If there are buildings, places or facilities in the organization that are not included in the scope of ISMS, the customer organization should explain the appropriate reasons for its exclusion.
5. 6. 5确定资产范围和边界
Determination of asset scope and boundary
资产范围和边界的确定一般可根据确定的客户组织的业务、组织和物理边界进行确定。在确定客户组织的资产范围和边界时,宜考虑以下因素:
The scope and boundary of assets can generally be determined according to the business, organizational and physical boundaries of the customer organization. The following factors should be considered when determining the asset scope and boundary of the customer organization:
(1)资产范围宜包括软件资产、硬件资产、数据资产、文件资产、人员资产及服务资产 等方面;
Assets should include software assets, hardware assets, data assets, document assets, personnel assets and service assets;
(2) 客户组织 ISMS范围内的业务流程、组织与职能、物理范围内的所有资产均宜纳入 组织信息安全风险评估范围。
Business processes, organizations and functions within the scope of customer organization ISMS and all assets within the physical scope should be included in the scope of information security risk assessment.
5. 6. 6确定技术范围和边界
Determination of technical scope and boundary
技术范围和边界主要是指客户组织所使用的信息与通信技术(ICT)和其它技术的范围和边界,一般可以通过识别组织使用的信息系统的方法进行确定。组织为支持其业务运行而进行的存储、处理或传输关键信息的各类信息系统一般宜纳入组织ISMS范围。组织信息系统可能跨越组织边界甚至国界,在这种情况下,确定组织信息系统的范围应考虑以下因素:
Technology scope and boundary mainly refers to the scope and boundary of information and communication technology (ICT) and other technologies used by customer organization, which can be determined by identifying information system used by organization. All kinds of information systems that store, process or transmit key information to support its business operation should be included in the scope of the organization's ISMS. Organizational information system may cross organizational boundaries or even national boundaries. In this case, the following factors should be considered in determining the scope of organizational information system:
1)社会文化环境;
Social and cultural environment;
2)适用的法律法规及合同要求;
Applicable laws and regulations and contract requirements;
3)对关键职责的责任;
Responsibility for key responsibilities;
4)技术约束(如:可用的带宽、服务的可用性等)。在考虑到以上因素后,适用时组织技术范围和边界的确定应包括以下描述:
Technical constraints (such as available bandwidth, availability of services, etc. ). Taking into account the above factors, the determination of the technical scope and boundary of the organization shall include the following description when applicable:
(1)组织负有管理职责的包含不同技术(例如无线、有线或数据/语音网络)的通信设施
Communication facilities with different technologies (e. g. , wireless, wired, or data / voice networks) with management responsibilities
(2)组织边界内的被组织控制和使用的软件;
Software controlled and used by the organization within the boundaries of the organization;
(3)网络、应用或生产系统所要求的信息通信技术硬件;
Information and communication technology hardware required by network, application or production system;
(4)与信息通信技术硬件、网络和软件有关的角色和职责。 当上述内容不是由组织自行控制时,受审核组织应在文件中清晰界定对第三方的依从关系。对于任何由组织所管理的、但被排除在ISMS范围之外的信息通信技术,应提供排除的理由。
Roles and responsibilities related to ICT hardware, networks and software. When the above contents are not controlled by the organization itself, the audited organization shall clearly define the compliance relationship with the third party in the document. For any ICT managed by the organization but excluded from the scope of ISMS, reasons for exclusion shall be provided.
5. 6. 7组织ISMS范围和边界的综合描述
Comprehensive description of scope and boundary of organization ISMS
以上五个方面的范围和边界是相互渗透、紧密联系的。综合以上五个方面的范围和边界后,组织ISMS的范围和边界可从以下方面进行描述:
The scope and boundary of the above five aspects are mutually penetrating and closely related. The scope and scope of ISMS can be described from the following five aspects:
(1)组织的关键特征(组织的职能部门、组织结构、服务、资产以及各资产的责任
Key characteristics of the organization (functional departments, organizational structure, services, assets and responsibilities of each asset
(2)范围和边界等);
Scope and boundary, etc. );
(3)范围内的组织的过程;
The process of organization within the scope;
(4)范围内的设备和网络的配置;
Equipment and network configuration within the scope;
(5)范围内的信息资产列表;
List of information assets within the scope;
(6)范围内的信息通信技术资产(例如服务器)列表;
List of ICT assets (e. g. servers) in scope;
(7) 范围内的场所位置图,并指出组织 ISMS的物理边界;
The physical boundary of the organization ISMS is pointed out;
(8) ISMS范围内的角色和职责描述,以及其与组织结构的关系; (9) 对于 ISMS范围的任何删减的细节和正当性理由。
Description of roles and responsibilities within the scope of ISMS and their relationship with organizational structure; (9) Details and justification of any deletion from the scope of ISMS.
5. 7认证证书格式执行《认证证书、认证标志、审核报告使用及证书状态声明规则》
The format of certification certificate shall be in accordance with the Rules for Certificate status statement,Use of the Certificate, Certification Mark and Audit Report.
5. 8注册资格保持Maintenance of registration qualification
对获证组织注册资格保持、暂停、撤销或缩小认证范围的管理执行《授予、保持、更新、扩大、缩小、暂停和撤销认证的管理程序》的要求。另外,如果发现受审核组织不允许接触信息资产或无法满足受审核组织关于基础信息资产的相关要求时,BOHAN在评估其对审核和认证的影响后可缩小认证范围或暂停或撤销注册资格。
The management of maintaining, suspending, revoking or narrowing the scope of certification of the certified organization shall be in accordance with the requirements of the administrative procedures for granting, maintaining, updating, expanding, narrowing, suspending and revoking certification. In addition, if it is found that the audited organization does not allow access to information assets or fails to meet the relevant requirements of the audited organization on basic information assets, BOHAN can reduce the scope of certification or suspend or revoke the registration qualification after assessing its impact on audit and certification.
6引用文件References
(1)CNAS-CC01:2015《管理体系认证机构要求》
CNAS-CC01:2015 requirements for management system certification bodies
(2)CNAS-CC170:2015《信息安全管理体系认证机构要求》
CNAS-CC170:2015 requirements for certification body of information security management system
(3)CNAS-SC170:2017《信息安全管理体系认证机构认可方案》
CNAS-SC170:2017 accreditation scheme for information security management system certification bodies
(4)G-BOHAN-UD-08 《能力分析评价系统管理程序》
G-BOHAN-UD-08 management procedure for capability analysis and evaluation system
(5)G-BOHAN-UD-09《认证审核管理程序》
G-BOHAN-UD-09 management procedure for certification and audit
(6)G-BOHAN-WI-01《审核方案策划管理办法》
G-BOHAN-wi-01 management measures for audit scheme planning
(7)G-BOHAN-UD-10《认证证书转换管理程序》
G-BOHAN-UD-10 Procedure for Administration of Certificate Transfer
(8)G-BOHAN-UD-11《授予、保持、更新、扩大、缩小、暂停和撤销认证的管理程序》
G-BOHAN-UD-11 management procedures for granting, maintaining, updating, expanding, reducing, suspending and revoking certification
(9)G-BOHAN-UD-14《认证决定管理程序》
G-BOHAN-UD-14 certification decision management procedure
(10)G-BOHAN-OD-06《认证证书、认证标志、审核报告使用及证书状态声明规则》
G-BOHAN-OD-06 Rules for Certificate status statement,Use of the Certificate, Certification Mark and Audit Report
(11)IAF MD 26:2023 TRANSITION REQUIREMENTS FOR ISO/IEC 27001:2022
(12)ISO/IEC 27006:2015 Information technology—Security techniques —Requirements for bodies providing audit and certification of information security management systems.
7记录表单Record form
(1)BOHAN-MF-117 《认证人员登记表》
BOHAN-MF-117 certification personnel registration form
(2)BOHAN-MF-148 《审核经历汇总表》
BOHAN-MF-148 summary of audit experience
(3)BOHAN-MF-145《认证人员专业能力评价表》
BOHAN-MF-145 evaluation form of professional competence of certified personnel
(4)BOHAN-MF-143《审核员认证管理人员专业能力测试表》
BOHAN-MF-143 professional competence test form for auditor certification management personnel
(5)BOHAN-MF-153 《CCAA注册管理体系审核员见证评审报告》
BOHAN-MF-153 "CCAA registration management system auditor witness review report"
附录A Appendix A
ISMS认证业务范围分类与分级
Classification and classification of ISMS certification business scope
大类 categories | 中类 Middle class | 级别 level | 描述 describe | 备注 remarks |
01 | 政务Government affairs | |||
01. 01 | 一 The 1st level | 国家机构 State institutions | 包括人大、政府、法院、检察院等,不含税务机关和海关 It includes the people's Congress, the government, the court and the procuratorate, excluding the tax authorities and customs | |
01. 02 | 一 The 1st level | 税务机关 Tax authority | ||
01. 03 | 一 The 1st level | 海关 Customs | ||
01. 04 | 一 The 1st level | 其他 Other | 例如政党,政协,社会团体等 For example, political parties, CPPCC, social organizations, etc | |
02 | 公共Public | |||
02. 01 | 一 The 1st level | 通信、广播电视 Radio and television | ||
02. 02 | 一 The 1st level | 新闻出版 Press and Publications | 包括互联网内容的提供 Including the provision of Internet content | |
02. 03 | 二 The 2nd level | 科研 scientific research | 涉及特别重大项目的应提升为一级 Those involving particularly important projects should be upgraded to The 1st level | |
02. 04 | 二 The 2nd level | 社会保障 social security | 例如社会保险基金管理、慈善团体等。包括医疗保险 For example, social insurance fund management, charitable organizations, etc. Including medical insurance | |
02. 05 | 二 The 2nd level | 医疗服务 medical service | ||
大类 categories | 中类 Middle class | 级别 level | 描述 describe | 备注 remarks |
02. 06 | 三 The 3rd level | 教育 education | ||
02. 07 | 三 The 3rd level | 其他 other | 例如市政公用事业(水的生产和供应、污水处理、燃气生产和供应、热力生产和供应、城市水陆交通设施的维护管理等) For example, municipal utilities (water production and supply, sewage treatment, gas production and supply, thermal production and supply, maintenance and management of urban land and water transportation facilities, etc. ) | |
03 | 商务business affairs | |||
03. 01 | 一 The 1st level | 金融 Finance | 例如银行、证券、期货、保险、资产管理等 For example, banking, securities, futures, insurance, asset management, etc | |
03. 02 | 一 The 1st level | 电子商务 Electronic Commerce | 以在线交易为主要特点,含网络游戏 Online trading is the main feature, including online games | |
03. 03 | 一 The 1st level | 物流 Logistics | 包括邮政 Including post | |
03. 04 | 三 The 3rd level | 咨询中介 Consulting agency | 例如法律、会计、审计、公证等 For example, law, accounting, auditing, notarization, etc | |
03. 05 | 三 The 3rd level | 旅游、宾馆、饭店 Tourism, hotels, restaurants | ||
03. 06 | 三 The 3rd level | 其他 Other | ||
04 | 产品的生产Production of products | |||
04. 01 | 一 The 1st level | 电力 Power | 包括发电和输、变、配电等 Including power generation and transmission, transformation, distribution, etc | |
04. 02 | 一 The 1st level | 铁路 Railway | ||
04. 03 | 一 The 1st level | 民航 Civil Aviation | ||
04. 04 | 一 The 1st level | 化工 Chemical industry | ||
04. 05 | 一 The 1st level | 航空航天 Aerospace | ||
04. 06 | 一 The 1st level | 水利 Water conservancy | ||
04. 07 | 二 The 2nd level | 交通运输 Transportation | 包括公路、水路、城市公共客运交通等,不含航空和铁路 Including roads, waterways, urban public passenger transport, etc. , excluding aviation and railway | |
04. 08 | 二 The 2nd level | 信息与通信技术 Information and communication technology | 例如软、硬件生产及其服务,系统集成及其服务,数字版权保护等 For example, software and hardware production and services, system integration and services, digital copyright protection, etc | |
04. 09 | 二 The 2nd level | 冶金 Metallurgy | ||
04. 10 | 二 The 2nd level | 采矿 Mining | 含石油、天然气开采 Oil and gas exploitation | |
04. 11 | 二 The 2nd level | 食品、药品、烟草 Food, medicine, tobacco | ||
04. 12 | 三 The 3rd level | 农、林、牧、副、渔业 Agriculture, forestry, animal husbandry, sideline and fishery | ||
04. 13 | 三 The 3rd level | 其他 Other | ||
附录B Appendix B
下表明确了与信息安全管理体系认证活动有关的人员的知识和技能的类型,“√”指认证机构应确定相应的知识和技能的准则和深度。“√ ”表示需要相对较深的知识和技能。
The following table defines the types of knowledge and skills of personnel related to information security management system certification activities, "√" refers to the criteria and depth for certification bodies to determine the corresponding knowledge and skills. "√ " indicates the need for relatively deep knowledge and skills.
知识和技能 Knowledge and skills | 认证职能Certification function | |||
实施申请评审以确定所需的审核组能力、选择审核组成员并确定审核时间 Conduct application review to determine the required audit team capability, select audit team members and determine the audit time | 复核审核报告并作 Review the audit report and make 出认证决定 Certification decision | 审核 Auditing | 领导审核组 Lead audit team | |
业务管理实践的知识 Knowledge of business management practices | √ | √ | ||
审核原则、实务和技巧的知识 Knowledge of audit principles, practices and techniques | √ | √ | √ | |
ISMS管理体系标准和(或)规范的知识 Knowledge of ISMS management system standards and / or specifications | √ | √ | √ | √ |
认证机构过程的知识 Knowledge certification process of certification body | √ | √ | √ | √ |
客户的业务领域的知识 Knowledge of the customer's business area | √ | √ | √ | √ |
客户的产品、过程和组织的知识 Customer knowledge of products, processes and organizations | √ | √ | √ | √ |
信息安全管理术语、原则、实践和技术 Information Security Management Terminology, Principles, Practices and Techniques | √ | √ | √ | |
与客户组织中的各个层级相适应的语言技能 Language skills appropriate to all levels of the customer organization | √ | √ | ||
作记录和撰写报告的技能 Skills in recording and writing reports | √ | √ | ||
表达技能Expression skills | √ | √ | ||
面谈技能 Interview skills | √ | √ | ||
审核管理技能 Audit management skills | √ | √ | ||
附录C. 1审核时间表
Appendix C. 1 audit schedule
雇员数量Number of employees | QMS初次审核审核时间(审核人日) Audit Time of QMS initial audit (auditor day) | EMS初次审核审核时间(审核人日) Audit Time of EMS initial audit (auditor day) | ISMS初次审核审核时间(审核人日) Audit Time of ISMS initial audit (auditor day) | 增加或减少的因素 Factors that increase or decrease | 总审核时间 Total audit time |
1~10 | 2 | 3 | 5 | ||
11~25 | 3 | 7 | |||
26~45 | 4 | 6 | 8. 5 | ||
46~65 | 5 | 10 | |||
66~85 | 6 | 11 | |||
86~125 | 7 | 8 | 12 | ||
126~175 | 8 | 13 | |||
176~275 | 9 | 14 | |||
276~425 | 10 | 15 | |||
426~625 | 11 | 12 | 16. 5 | ||
626~875 | 12 | 17. 5 | |||
876~1175 | 13 | 18. 5 | |||
1176~1550 | 14 | 19. 5 | |||
1551~2025 | 15 | 18 | 21 | ||
2026~2675 | 16 | 22 | |||
2676~3450 | 17 | 23 | |||
3451~4350 | 18 | 24 | |||
4351~5450 | 19 | 25 | |||
5451~6800 | 20 | 26 | |||
6801~8500 | 21 | 27 | |||
8501~10700 | 22 | 28 | |||
>10700 | 沿用以上规律 Follow the above rules | 沿用以上规律 Follow the above rules |
附录 C. 2审核时间
Appendix C. 2 audit time
本附录为确定ISMS审核时间的程序提供了最低要求和指南。
This appendix provides the minimum requirements and guidance for the procedures for determining the timing of ISMS audits.
策划人员应针对每一个客户及其被认证的 ISMS,识别初次认证、监督审核和再认证
The Planner shall identify the initial certification, supervisory audit and recertification for each customer and its certified isms
审核所需花费的审核时间。在审核策划阶段,使用本附录可以确保使用一致的方法来确定适当的审核时间。此外,可以根据审核过程(尤其是第一阶段)的发现(如:ISMS 范围的复杂度的不同评价结果,或范围中增加的场所)来调整审核时间。
Audit time required for the audit. During the audit planning phase, the use of this appendix ensures that a consistent approach is used to determine the appropriate audit time. In addition, the audit time can be adjusted according to the findings of the audit process (especially the first stage), such as the different evaluation results of the complexity of the scope of ISMS, or the increased sites in the scope).
本附录阐述了:
This appendix describes:
用于审核时间计算的概念;
Concept for audit time calculation;
确定不同审核阶段所需时间的程序的要求。
The requirements of the procedure for determining the time required for different audit stages.
C2. 1概念Concept
C2. 1. 1雇员 Employees
是指其工作活动与ISMS范围有关的所有人员。所有班次雇员的总数是确定审核时间的起点。
Refers to all personnel whose work activities are related to the scope of ISMS. The total number of employees on all shifts is the starting point for determining the audit time.
雇员的有效数量包括审核期间在场的非长期(季节性的、临时的及分包的)员工。认证机构宜与拟审核的组织就最好地反映组织全部范围的审核时间达成一致意见。适当时,可考虑季度、月份、星期、日期和班次。
The effective number of employees includes non permanent (seasonal, temporary and sub contracted) employees present during the audit. The certification body should agree with the organization to be audited on the audit timing that best reflects the full scope of the organization. Quarter, month, week, date and shift may be considered when appropriate.
对于非全日制雇员,宜根据其工作小时数与全日制雇员的比较,并比照全日制雇员处理。
For part-time employees, it is better to compare their working hours with that of full-time employees and treat them with reference to full-time employees.
C2. 1. 2审核时间 Audit time
审核员或审核组策划和编制报告和现场审核所使用的时间,其中包括接触组织、人员、记录、文件和过程所用的时间。
The time used by auditors or audit teams to plan and prepare reports and on-site audits, including time spent contacting organizations, personnel, records, documents and processes.
C2. 2确定初次认证审核时间Determine the initial certification audit time
C2. 2. 1总则 General
审核时间的计算,应遵从文件化的程序
The calculation of audit time shall follow the documented procedure
C2. 2. 2 审核时间的计算 Review of calculation time
表 C. 1 给出了初次审核天数平均值的起点(在此处及后面的内容中,这个数值包括
Table C. 1 gives the starting point of the average number of days of initial audit (here and later, this value includes
一次初次审核(第一阶段和第二阶段)的天数)。经验表明,对于一个覆盖了给定数量的、在组织控制下工作的人员的 ISMS 范围来说,这一数值是适当的。经验还表明,对于相似规模的 ISMS 范围,有些需要多的审核时间,有些需要少的审核时间。
The number of days of an initial audit (phase I and phase II). Experience has shown that this value is appropriate for an ISMS range covering a given number of people working under the control of the organization. Experience has also shown that for ISMS of similar size, some require more audit time and some require less audit time.
表 C. 1 提供了审核策划应使用的框架。该表基于在组织控制下工作的、所有班次的
Table C. 1 provides the framework to be used for audit planning. The table is based on all shifts working under the control of the organization
人员的总数来识别审核时间的起点,然后根据适用于所审核的 ISMS 范围的重要因素来调整它,并对每一个因素赋予增、减权重以修正基数。使用表 C. 1 时应考虑促成因素和最大偏移的限制。
The starting point of audit time is identified by the total number of personnel, and then it is adjusted according to the important factors applicable to the scope of ISMS being audited, and each factor is given an increase or decrease weight to modify the base. The constraints of contributing factors and maximum offset should be considered when using table C. 1.
C2. 2. 3调整审核时间的因素 Factors for adjusting audit time
a) 复杂的后勤,在 ISMS 范围中涉及不止一处建筑物或地点
Complex logistics involving more than one building or location within the scope of ISMS
b) 员工所说的语言超过一种(需要翻译或审核员个人无法独立工作),提供的 文件使用了一种以上的语言
The employee speaks more than one language (translation is required or the auditor cannot work independently), and the documents provided use more than one language;
c) 为了确认管理体系认证范围内永久场所的活动,需要访问临时场所的活动;
In order to confirm the activities of permanent sites within the scope of management system certification, it is necessary to visit the activities of temporary sites;
d) 适用于 ISMS 的标准和法规数量很多;
There are many standards and regulations applicable to ISMS;
允许减少审核时间的因素,例如:
Factors that allow for reduced audit time, such as:
a) 没有风险或者低风险的产品/过程;10%
Products / processes with no or low risk; 10%
b) 产品提供或服务提供过程仅包含单一的一般性活动(如服务类型); 10%
The process of product or service provision contains only a single general activity (e. g. service type); 10%
c) 产品提供或服务提供过程中相当一部分员工从事相似的简单职能; 10%
In the process of providing products or services, a considerable number of employees are engaged in similar simple functions; 10%
d) 我机构对客户管理体系已有的了解(例如已获得我机构其他体系认证); 10%
Our organization's existing understanding of customer management system (for example, we have obtained other system certification of our organization); 10%
e) 客户为认证所作的准备(例如已经获得过其他认证机构认证); 10%
Customer's preparation for certification (e. g. having been certified by other certification bodies); 10%
f) 高度成熟的管理体系。10%
Highly mature management system. 10%
在认证客户或被获证组织在临时场所提供其产品或服务时,将对这类场所的评价纳入到认证审核和监督方案中是十分重要的。
It is very important to incorporate the evaluation of such sites into the certification audit and supervision program when the certified customer or the accredited organization provides its products or services in temporary sites.
宜考虑上述因素,并根据这些因素对审核时间做出调整。这些因素可证实一次有效审核所需要更多或更少的审核时间的合理性。增加时间的因素可被减少时间的因素冲抵。在任何情况下,对审核时间表中的时间的调整,应保持足够的证据和记录来证实其变化的合理性。
These factors should be considered and adjusted according to the above factors. These factors can justify the need for more or less audit time for an effective audit. The factor of increasing time can be offset by the factor of reducing time. In any case, adjustments to the time in the audit schedule, Sufficient evidence and records should be kept to verify the rationality of the changes.
C2. 2. 4 对审核时间偏离的限制Limitation on audit time deviation
为了确保能够实施有效的审核并确保可靠和可比较的结果,对表C. 1中初次认证审核时间的减少,不应超过30%。应确定偏离审核时间表的适当理由,并形成文件。
In order to ensure effective audit and reliable and comparable results, the reduction of the initial certification audit time in table C. 1 should not exceed 30%. Appropriate reasons for deviation from the audit schedule should be identified and documented.
C2. 2. 5 现场审核时间On site audit time
策划和编制报告一起所用的“审核时间”通常不宜使总的现场“审核时间”减少到表C. 1中“总审核时间”的70%以下。当策划和编制报告需要增加时间时,不能以此为由而减少现场审核时间。审核员旅途时间未计在内,这应在表中所给出的审核时间的基础上另外增加。
The "audit time" used together with the planning and preparation of the report should not normally reduce the total on-site "audit time" to less than 70% of the "total audit time" in table C. 1. When the planning and preparation of the report need to increase the time, we can not reduce the on-site audit time for this reason. The auditor's travel time is not included, This should be added to the audit time given in the table.
注 1:70%是基于ISMS审核经验所考虑的因素。
Note 1: 70% is based on ISMS audit experience.
C2. 2. 6 远程审核Remote audit
如果使用了远程审核技术(例如,交互式基于网络的协作、网络会议、电话会议和/或组织过程的电子验证)与客户组织接触,这些活动宜在审核计划中加以识别(见本文件的 IS 9. 1. 5),可以考虑将其作为现场审核时间的一部分。
If remote audit techniques (e. g. , interactive web-based collaboration, web conferencing, teleconference, and / or electronic verification of organizational processes) are used to contact the customer organization, these activities should be identified in the audit plan (see is 9. 1. 5 of this document) and can be considered as part of the on-site audit time.
如果认证机构审核计划中远程审核活动占据大于30%的现场审核时间,认证机构宜有理由证明审核计划是适当的,并在实施前得到认可机构的专门批准。
If the remote audit activities in the certification body audit plan occupy more than 30% of the on-site audit time, the certification body should have reasons to prove that the audit plan is appropriate and obtain special approval from the accreditation body before implementation.
注2:现场审核时间是指分配给单独场所的现场审核时间。远程场所的电子审核被视为远程审核,即使电子 审核是在组织的物理场所进行。
Note 2: site audit time refers to the on-site audit time allocated to a separate site. Electronic auditing at a remote location is considered a remote audit, even if it is conducted at the physical site of the organization.
C2. 3 监督审核的审核时间Audit time of supervision audit
在初次认证审核周期,对一个组织的监督时间宜与初次审核时间成比例,每年用于监督审核的时间总量大约是初次审核时间的1/3。认证机构宜适时地核查其所策划的监督审核时间,以考虑组织的变更及管理体系的成熟度等,至少宜在再认证审核时进行该核查。
In the initial certification audit cycle, the supervision time of an organization should be proportional to the initial audit time, and the total amount of time used for supervision and audit is about 1 / 3 of the initial audit time. The certification body should timely check the planned supervision and audit time to consider the changes of the organization and the maturity of the management system. At least, the verification should be carried out during the re certification audit.
C2. 4 再认证的审核时间Time of recertification
用于再认证审核的全部时间还取决于本文件 IS 9. 1. 6及 CNAS-CC01:2015的9. 4中所确定活动的结果。再认证审核所需的时间宜与同一组织的初次认证审核所用的时间成比例,大约是初次认证审核时间的2/3。再认证审核时间遵照上述并超出例行的监督审核时间,但当再认证审核与计划的例行监督审核一起实施时,再认证审核也要满足监督审核的要求。
The total time spent on the recertification audit also depends on the results of the activities identified in is 9. 1. 6 of this document and 9. 4 of CNAS-CC01:2015. The time required for recertification audit should be proportional to the time spent in the initial certification audit of the same organization, which is about 2 / 3 of the time of the initial certification audit. The re certification audit time follows the above and exceeds the routine supervision audit time, However, when the recertification audit is carried out together with the planned routine supervision audit, the re certification audit shall also meet the requirements of the supervision and audit.
C. 3审核时间计算方法 Calculation method of audit time
C. 3. 1 总则 General
本附录为获得一个审核时间计算公式提供了进一步的指南。C. 3. 2 给出了一个对因数
This appendix provides further guidance for obtaining a formula for calculating audit time. C. A pair factor is given in 3. 2
进行分类的示例,它可用作审核时间计算的基础。C. 3. 3 提供了一个审核时间计算的示例。
An example of classification, which can be used as the basis for audit time calculation. C. 3. 3 provides an example of audit time calculation.
C. 3. 2 审核时间计算因数的分类
Classification of audit time calculation factors
表中给出了对主要的审核时间计算因数进行分类的示例。认证机构可以使用该分类来获得一个符合要求的审核时间计算方案。
Examples of classification of the main audit time calculation factors are given in the table. Certification authority can use this classification to obtain a satisfactory audit time calculation scheme.
审核时间计算因数的分类
Classification of audit time calculation factors
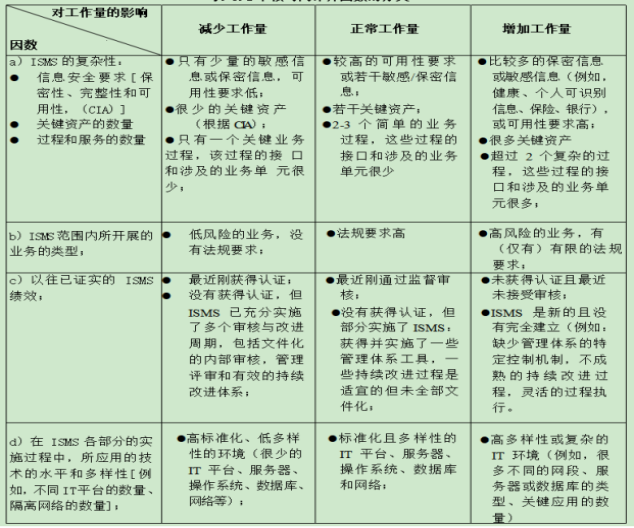
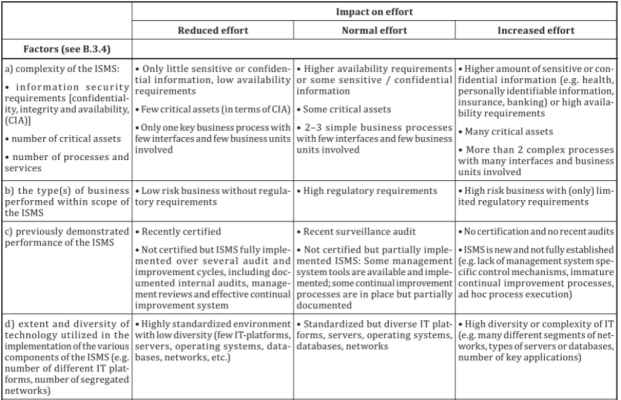


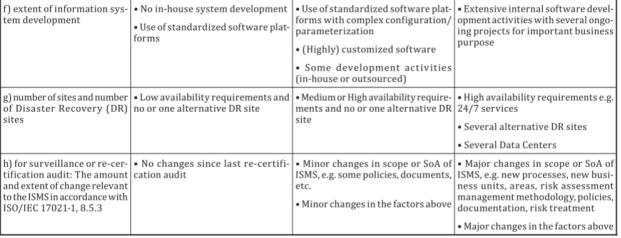
C. 3. 3 审核时间计算的示例
C. 3. 3 example of audit time calculation
以下示例阐述了认证机构如何使用 C. 3. 2 中的因数来计算审核时间。该示例中的审核
The following example illustrates how the certification authority uses the factors in c. 3. 2 to calculate audit time. Auditing in this example
时间计算,是按照以下方法进行的:
Time calculation is carried out according to the following methods:
第一步:确定与业务和组织相关的(非 IT)因数。识别表 中每个类别的适宜分值,并对结果求和;
Identify business and organization related (non it) factors. Identify the appropriate score of each category in the table and sum the results;
第二步:确定与 IT 环境相关的因数。识别表中每个类别的适宜分值,并对结果求和;
Determine factors related to the IT environment. Identify the appropriate score of each category in the table and sum the results;
第三步:基于以上第一步和第二步的结果,通过选择表中的适宜条目,识别这些因数对审核时间的影响;
Based on the results of the first and second steps above, identify the impact of these factors on the audit time by selecting appropriate items in the table;
第四步:最终计算。将由审核时间表(表 C. 1)所确定审核人天数乘以第三步中得出的系数。当利用多场所抽样时,要根据执行多场所抽样计划所需的工作量增加所计算出的审核人天。
Final calculation. Multiply the number of auditor days determined by the audit schedule (table C.1) by the coefficient obtained in step 3. When multi site sampling is used, the calculated reviewer days shall be increased according to the workload required to implement the multi site sampling plan.
这个结果是最终需要调整的审核人天数。
This result is the number of reviewer days that need to be adjusted eventually.
与业务和组织(非 IT)相关的因数 Business and organizational (non it) related factors
类别category | 分值Score |
业务类型和法规要求 Business types and regulatory requirements | 1. 组织所处的是一个非关键业务领域,且不受管制的领域。a The organization is in a non critical business area and is not regulated. a 2. 组织的客户处于关键业务领域;a The organization's customers are in key business areas; a 3. 组织处于关键业务领域;a The organization is in key business areas; a |
过程与任务 Process and task | 1. 一般的过程,涉及一般的且重复性的任务;大量在组织控制下工作的人员从事相同的任务;很少的产品或服务; General process, involving general and repetitive tasks; A large number of people working under the control of the organization are engaged in the same task; Products or services with few products; 2. 一般的但不重复的过程,涉及大量的产品或服务。 A general but non repetitive process involving a large number of products or services. 3. 复杂的过程,大量的产品和服务,许多业务单元包含在认证范围内 Complex process, a large number of products and services, many business units are included in the scope of certification (ISMS 涉及复杂性高的过程,或数量相对较大的活动,或独特的活动)。 (ISMS involves highly complex processes, or relatively large number of activities, or unique activities). |
管理体系的建立水平 Establishment level of management system | 1. 已经很好地建立了 ISMS,和(或)存在其他管理体系; ISMS has been well established and / or other management systems exist; 2. 其他管理体系的要素,有些已经实施,有些没有实施; Some of the other elements of the management system have been implemented and some have not been implemented; 3. 根本没有实施其他管理体系,ISMS 是新且没有建立。 No other management system has been implemented, ISMS is new and not established. |
a:关键业务领域是可以影响关键公共服务的领域,这些公共服务将引起健康、安全、经济、形象和 政府运行能力的风险,从而可能对国家造成非常重大的负面影响。 a: Key business areas are areas that can affect key public services. These public services will cause risks in health, safety, economy, image and government operation capacity, which may have a very significant negative impact on the country. | |
与 IT 环境相关的因数 Factors related to it environment
类别category | 分值Score |
IT 基础设施的复杂程 度 Complexity of IT infrastructure | 1. 很少的或高度标准化的 IT 平台、服务器、操作系统、数据库、网络等; Few or highly standardized it platforms, servers, operating systems, databases, networks, etc; 2. 多个不同的 IT 平台,服务器、操作系统、数据库、网络; Multiple different IT platforms, servers, operating systems, databases, networks; 3. 很多不同的 IT 平台、服务器、操作系统、数据库、网络。 Many different IT platforms, servers, operating systems, databases, networks. |
对外包和供应商(包括云服务)的依赖程度 Dependence on outsourcing and suppliers (including cloud services) | 1. 很少或不依赖外包或供应商; Little or no reliance on outsourcing or suppliers; 2. 有些依赖外包或供应商,这些外包或供应商与某些重要业务活动相关,但不是与所有的重要业务活动相关; Some rely on outsourcing or suppliers, which are related to some important business activities, but not all important business activities; 3. 高度依赖外包或供应商,外包或供应商对重要业务活动有着很大影响。 Highly dependent on outsourcing or suppliers, outsourcing or suppliers have a great impact on important business activities. |
信息系统开发 Information system development | 1. 没有或非常有限的内部系统/应用开发; No or very limited internal system / application development; 2. 有一些服务于某些重要业务目的的、内部的或外包的系统/应用开发; There are some systems / application development that serve some important business purposes, internal or outsourcing; 3. 有大量服务于重要业务目的的、内部的或外包的系统/应用开发。 There are a large number of system / application development services for important business purposes, internal or outsourcing. |
因数对审核时间的影响 Influence of audit time factor
IT 复杂性 业务复杂性 II complexity business complexity | 低low(3-4) | 中medium(5-6) | 高high(7-9) |
高high(7-9) | 5 % ~ 20 % | 10 % ~ 50 % | 20 % ~ 100 % |
中medium(5-6) | -5 % ~ −10 % | 0 % | 10 % ~ 50 % |
低low(3-4) | -10 % ~ −30 % | -5 % ~ −10 % | 5 % ~ 20 % |
附录D Appendix D
信息安全管理体系审核员技术能力评价准则
Evaluation criteria for technical competence of auditors of information security management system
D. 1信息技术评价准则 D. 1 information technology evaluation criteria | ||||
要素描述Element description | 等级Grade | |||
一级 Level 1 | 二级 Level 2 | 三级 Level 3 | ||
信息技术基础Fundamentals of information technology | ||||
通讯技术基础 Fundamentals of communication technology (包括网络通讯和传统通讯技术) (including network communication and traditional communication technology) | 网络通讯原理、传统通讯原理、TCP/IP协议族 Network communication principle, traditional communication principle, TCP / IP protocol family | 掌握 master | 熟悉 be familiar with | 了解 understand |
典型的通讯环境、典型通讯问题 Typical communication environment, typical communication problems | 掌握 master | 掌握 master | 熟悉 be familiar with | |
计算机技术基础 Fundamentals of computer technology | 计算机原理、操作系统、数据库原理 Computer principle, operating system, database principle | 掌握 master | 掌握 master | 熟悉 be familiar with |
系统集成 system integration | 系统集成的基本方法与项目管理方法、系统集成方案设计、典型的系统集成工程 Basic method and project management method of system integration, system integration scheme design, typical system integration engineering | 掌握 master | 掌握 master | 熟悉 be familiar with |
软件工程 software engineering | 软件工程基本思想 Basic idea of software engineering | 掌握 master | 掌握 master | 熟悉 be familiar with |
软件项目实施、软件开发管理相关国家标准 Software project implementation, software development and management related national standards | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | |
CMMi CMMi | 熟悉 be familiar with | 了解 understand | 了解 understand | |
信息技术应用Application of information technology | ||||
通用支撑平台 General support platform (操作系统、数据库、中间件) (operating system, database, middleware) | 常用的操作系统 Common operating systems | 掌握 master | 掌握 master | 熟悉 be familiar with |
典型操作系统的适用环境 Application environment of typical operating system | 掌握 master | 熟悉 be familiar with | 了解 understand | |
应用支撑平台分层、主流的应用支撑平台、主流数据库、操作系统、应用支撑平台和数据的主要安全问题 Application support platform layering, mainstream application support platform, mainstream database, operating system, application support platform and main security issues of data | 掌握 master | 熟悉 be familiar with | 了解 understand | |
主流软件开发平台 Mainstream software development platform | 主流软件开发平台、主要软件测试工具 Mainstream software development platform, main software testing tools | 掌握 master | 熟悉 be familiar with | 了解 understand |
IT服务管理 It service management | IT 服务管理基本思想、 IT服务管理流程、典型 IT服务管理工具 It service management basic idea, it service management process, typical IT service management tool | 掌握 master | 熟悉 be familiar with | 了解 understand |
典型大众化应用 Typical popular application | 典型的大众化应用系统(如OA、网站、邮件系统、即时通讯系统、ERP等) Typical popular application systems (such as OA, website, email system, instant messaging system, ERP, etc. ) | 掌握 master | 熟悉 be familiar with | 了解 understand |
D. 2信息安全技术评价准则 D. 2. Evaluation criteria of information security technology | |||||
要素描述Element description | 等级Grade | ||||
一级 Level 1 | 二级 Level 2 | 三级 Level 3 | |||
A1信息安全风险管理A1 information security risk management | |||||
A1. 1信息安全风险评估 A1. Security information risk assessment 1 | 常见的风险评估方法 Common risk assessment methods | 掌握 master | 掌握 master | 掌握 master | |
典型资产的信息安全重要度 Information security importance of typical assets | 掌握 master | 熟悉 be familiar with | 了解 understand | ||
典型资产常见的脆弱性、威胁和风险 Common vulnerabilities, threats and risks of typical assets | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | ||
A1. 2信息安全风险处置 A1. 2. Information security risk disposal | 风险处置的基本要素和典型风险处置方法 The basic elements and typical methods of risk disposal | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | |
典型资产常见脆弱性的控制措施、典型资产常见威胁的防范措施、典型信息安全风险的防范措施 Control measures for common vulnerability of typical assets, preventive measures for common threats of typical assets, and preventive measures for typical information security risks | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | ||
A1. 3脆弱性管理 A1. 3 vulnerability management | 典型的操作系统漏洞及获取方式、典型的应用系统漏洞、系统漏洞的管理方法与工具 Typical operating system vulnerabilities and access methods, typical application system vulnerabilities, system vulnerability management methods and tools | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A2信息安全事件管理A2 information security incident management | |||||
A2. 1业务连续性管理 A2. 1 business continuity management | 业务连续性管理的信息安全方面要求 Information security requirements of business continuity management | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | |
业务连续性管理程序的要求 Requirements of business continuity management procedures | 掌握 master | 熟悉 be familiar with | 了解 understand | ||
业务连续性计划、业务连续性演练方案制定方法 Business continuity plan and business continuity exercise plan | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | ||
业务连续性演练分析、评价方法 Analysis and evaluation method of business continuity exercise | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | ||
典型的应急响应流程 Typical emergency response process | 掌握 master | 熟悉 be familiar with | 了解 understand | ||
A2. 2备份与恢复A2. 2 backup and recovery | |||||
A2. 2备份与恢复 A2. 2 backup and recovery | 主流的灾备技术、典型的灾备设备、典型的灾备管理规范、典型的灾备方案和环境 Mainstream disaster recovery technology, typical disaster recovery equipment, typical disaster recovery management specification, typical disaster recovery scheme and environment | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A3物理和环境安全A3 and physical security | |||||
A3. 1区域安全 A3. 1 regional security | 安全区域的划分原则 Principle of safety area division | 掌握 master | 熟悉 be familiar with | 了解 understand | |
安全区域的典型控制措施 Typical control measures in safe area | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | ||
A3. 2支持性设施与设备安全 A3. 2 supporting facilities and equipment safety | 典型的支持性设施与设备的作用与性能、典型的支持性设施与设备的维护与管理要求 Functions and performance of typical supporting facilities and equipment, maintenance and management requirements of typical supporting facilities and equipment | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | |
A4网络安全A4 network security | |||||
A4. 1边界防护 A4. 1 boundary protection | 网络环境与边界划分、典型的网络环境、典型的网络设备、典型的网络攻击手段、典型的边界防护技术 Network environment and boundary division, typical network environment, typical network equipment, typical network attack means, typical boundary protection technology | 掌握 master | 熟悉 be familiar with | 了解 understand | |
主流的计算环境 Mainstream computing environment | 熟悉 be familiar with | 了解 understand | 了解 understand | ||
A4. 2主机安全 A4. 2 host security | 典型的操作系统、典型的系统安全问题 Typical operating system, typical system security issues | 掌握 master | 熟悉 be familiar with | 熟悉 be familiar with | |
典型的系统安全加固技术 Typical system security reinforcement technology | 熟悉 be familiar with | 熟悉 be familiar with | 了解 understand | ||
A4. 3防范恶意和移动代 A4. 3. Guar码d against malicious and mobile agents code | 恶意和移动代码的基本原理、流行的恶意代码、恶意代码的防护技术、移动代码的使用规范 The basic principles of malicious and mobile code, popular malicious code, protection technology of malicious code, and usage specification of mobile code | 掌握 master | 熟悉 be familiar with | 了解 understand | |
主流的恶意代码检测、防护产品 Mainstream malware detection and protection products | 掌握 master | 了解 understand | 了解 understand | ||
A5访问控制A5 access control | |||||
A5. 1用户访问控制 A5. 1 user access control | 用户鉴别技术及主流产品 User identification technology and mainstream products | 掌握 master | 了解 understand | 了解 understand | |
典型的网络访问控制方式、典型的操作系统访问控制方式、典型的应用和信息(含数据库)访问控制 Typical network access control, typical operating system access control, typical application and information (including database) access control | 掌握 master | 熟悉 be familiar with | 了解 understand | ||
A5. 2移动计算和远程工作 A5. Mobile computing and remote working | 安全通讯协议、移动计算模式、远程工作模式、远程工作的典型问题 Security communication protocol, mobile computing mode, remote working mode and typical problems of remote work | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A6软件安全A6 software security | |||||
A6. 1软件安全开发 A6. 1 software security development | 软件安全设计与开发的过程管理、典型的应用软件安全问题、典型的应用软件安全控制措施、主要的应用软件安全测试点和安全测试工具 Software security design and development process management, typical application software security problems, typical application software security control measures, main application software security test points and security testing tools | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A6. 2软件安全测试 A6. 2 software security testing | 、典型的应用软件测试方法、主要的应用软件安全测试点和安全测试工具 The main software testing methods, security testing tools and application points | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A6. 3软件获取与分发管理 A6. 3 software acquisition and distribution management | 软件分发管理技术、典型的软件获取方式、典型的软件分发方式及工具 Software distribution management technology, typical software acquisition methods, typical software distribution methods and tools | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A6. 4软件安全审计 A6. 4 software security audit | 软件安全审计技术、应用软件的关键安全审计点、典型的应用软件安全审计工具 Software security audit technology, key security audit points of application software, and typical application software security audit tools | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A7密码技术A7 cryptography | |||||
A7. 1密码原理密钥管理 A7. Principle of cryptography key management | 密码基本原理、典型的密码算法、密钥管理技术、密码应用与密钥管理的相关要求 Basic principles of cryptography, typical cryptographic algorithms, key management technology, cryptographic application and key management requirements | 熟悉 be familiar with | 熟悉 be familiar with | 了解 understand | |
A7. 2公钥体系(PKI) A7. 2 public key system (PKI) | PKI基本原理和典型应用、RSA和ECC(两个典型算法)、CA证书及其管理、CA中心的管理要求 PKI basic principle and typical application, RSA and ECC (two typical algorithms), CA certificate and its management, management requirements of Ca center | 熟悉 be familiar with | 了解 understand | 了解 understand | |
A8信息安全建设A8 information security construction | |||||
A8. 1信息技术产品安全性 A8. 1 it product security | 信息技术产品安全性评价、信息技术产品安全性保障、配置管理与安全配置 It product security evaluation, it product security assurance, configuration management and security configuration | 熟悉 be familiar with | 熟悉 be familiar with | 了解 understand | |
A8. 2信息安全工程 A8. 2. Information security engineering | 信息安全工程概念、信息安全工程管理手段 Concept of information security engineering and management means of information security engineering | 掌握 master | 熟悉 be familiar with | 了解 understand | |
A8. 3信息安全产品 A8. Product safety information 3 | 主流的信息安全产品、信息安全产品的管理要求 Management requirements of mainstream information security products and information security products | 掌握 master | 了解 understand | 了解 understand | |


